- Splunk Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Re: Strange behavior of an eval
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
"call" OR "exception1" OR "exception2" OR "exception3"
| eval calls = if(like(message, "%call%"), 1, 0)
| eval errors1 = if(like(message, "%exception1%"), 1, 0)
| eval errors2 = if(like(message, "%exception2%"), 1, 0)
| eval errors3 = if(like(message, "%exception3%"), 1, 0)
| eval errors = errors1 + errors2 + errors3
| eval allErrorsPerMile = round((errors*1000) / calls, 3)
| stats sum(allErrorsPerMile), sum(errors1), sum(errors2), sum(errors3), sum(errors), sum(calls)
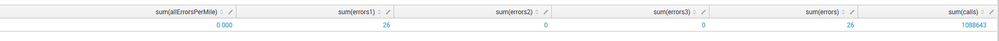
Straight to the point: "calls" eval do not work in calculations
allErrorsPerMile = round((errors*1000) / calls, 3)
even though im sure it contains some value(it can be seen on the screenshot)
Im also sure the
| eval allErrorsPerMile = round((errors*1000) / calls, 3)
works becouse if i put a number instead of "calls" it calculates it
Whats wrong there? maybe I should approach the problem differently?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The eval command running on a per-event basis. This part of your search string:
| eval calls = if(like(message, "%call%"), 1, 0)
is setting the value of
calls to either 1 or 0. So on some events, you are dividing by 0, which will produce an error.
So let's talk about these lines:
| eval errors = errors1 + errors2 + errors3
| eval allErrorsPerMile = round((errors*1000) / calls, 3)
Are you actually intending to calculate
allErrorsPerMile on a per-event basis? Or is this meant to be a value you are calculating across the sum of the errors in all events? If it's the latter, you'll need to do something like this instead:
| stats sum(errors1) AS errors1 sum(errors2) AS errors2 sum(errors3) AS errors3 sum(calls) AS calls | eval errors=errors1 + errors2 + errors3 | eval allErrorsPerMile=if(calls>0, round((errors*1000)/calls, 3), "Error: Trying to divide by zero")
By reversing the order of the stats and eval commands, you'll get totals across all events, rather than across individual events.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The eval command running on a per-event basis. This part of your search string:
| eval calls = if(like(message, "%call%"), 1, 0)
is setting the value of
calls to either 1 or 0. So on some events, you are dividing by 0, which will produce an error.
So let's talk about these lines:
| eval errors = errors1 + errors2 + errors3
| eval allErrorsPerMile = round((errors*1000) / calls, 3)
Are you actually intending to calculate
allErrorsPerMile on a per-event basis? Or is this meant to be a value you are calculating across the sum of the errors in all events? If it's the latter, you'll need to do something like this instead:
| stats sum(errors1) AS errors1 sum(errors2) AS errors2 sum(errors3) AS errors3 sum(calls) AS calls | eval errors=errors1 + errors2 + errors3 | eval allErrorsPerMile=if(calls>0, round((errors*1000)/calls, 3), "Error: Trying to divide by zero")
By reversing the order of the stats and eval commands, you'll get totals across all events, rather than across individual events.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The issue seems to be in output of eval errors
Can you tell me the output of errors? Is it coming propeR?