Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Splunk Search
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- Splunk Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Re: Regex to extract multiple fields from single e...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
gvnd
Path Finder
06-05-2017
04:41 AM
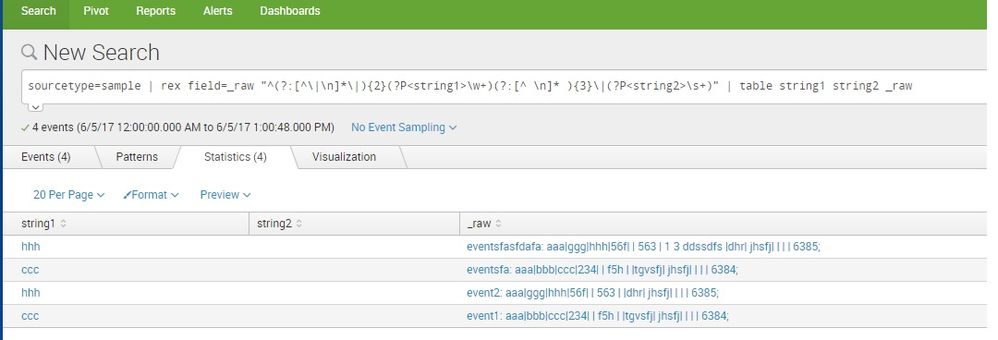
Hi, I want to extract particular fields from single event based on fields position.
Sample Data:
event1: aaa|bbb|ccc|234| | f5h | |tgvsfj| jhsfj| | | | 6384;
event2: aaa|ggg|hhh|56f| | 563 | |dhr| jhsfj| | | | 6385;
Now, I want to extract 3rd field(i.e ccc) and 7th field(i.e some spaces,nodata)
My data may include spaces.
I need regex to extract those fields only.
Thanks in advance.
1 Solution
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
dineshraj9
Builder
06-05-2017
04:57 AM
You see each field is a set of characters which is "NOT |" followed by a "|".
| rex "([^\|]*\|){2}(?<thirdField>[^\|]*)\|([^\|]*\|){3}(?<seventhField>[^\|]*)"
Test regular expressions using https://regex101.com/r/Odnybw/1
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
inventsekar

SplunkTrust
06-05-2017
05:04 AM
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
dineshraj9
Builder
06-05-2017
04:57 AM
You see each field is a set of characters which is "NOT |" followed by a "|".
| rex "([^\|]*\|){2}(?<thirdField>[^\|]*)\|([^\|]*\|){3}(?<seventhField>[^\|]*)"
Test regular expressions using https://regex101.com/r/Odnybw/1
Get Updates on the Splunk Community!
Detecting Remote Code Executions With the Splunk Threat Research Team
REGISTER NOWRemote code execution (RCE) vulnerabilities pose a significant risk to organizations. If ...
Observability | Use Synthetic Monitoring for Website Metadata Verification
If you are on Splunk Observability Cloud, you may already have Synthetic Monitoringin your observability ...
More Ways To Control Your Costs With Archived Metrics | Register for Tech Talk
Tuesday, May 14, 2024 | 11AM PT / 2PM ET
Register to Attend
Join us for this Tech Talk and learn how to ...