Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Splunk Search
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- Splunk Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Re: Parsing of highly nested JSON events with arra...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Parsing of highly nested JSON events with arrays
wfskmoney
Path Finder
04-20-2020
02:29 AM
We want to parse highly nested jsons into expanded tables. We found that the following code works, given we apply the | rename . as _ as many times as deep the nesting is. Without replacing the "." Splunk does not make all fields and subfields available. Might there be a more generic solution?
index="adm_compute_qcheck"
| rename *.* as *_* | rename *.* as *_* | rename *.* as *_* | rename *.* as *_*
| rename *_{}* as ** | rename *{}_* as ** | rename *{}_* as **
Here the first part of the JSON:
[
{
"BIOS": {
"manufacturer": "INSYDE Corp.",
"SystemBiosMajorVersion": 0,
"SystemBiosMinorVersion": 41,
"SMBIOSBIOSVersion": "0.99"
}
},
{
"Checkpoint": {
}
},
{
"ClusterName": null
},
{
"CPUType": {
"NumberOfCores": 16
}
},
{
"HBA": [
{
"active": true,
"drivername": "elxfc",
"driverversion": "12.2.207.0",
"firmwareversion": "11.4.204.25",
"optionromversion": "11.4.204.25",
"manufacturer": "Emulex Corporation",
"model": "LPe32002-AP",
"serialnumber": "FC83980875"
},
{
"active": true,
"drivername": "elxfc",
"driverversion": "12.2.207.0",
"firmwareversion": "11.4.204.25",
"optionromversion": "11.4.204.25",
"manufacturer": "Emulex Corporation",
"model": "LPe32002-AP",
"serialnumber": "FC83980875"
}
]
},
{
"HPE": [
]
},
{
"HPEDiskCount": 0
},
{
"HPELogicalDisks": {
"Status": null,
"RaidLevel": null,
"ID": null,
"Capacity": null
}
},
{
"HPEPhysicalDisks": [
]
},
{
"Mig": {
"VirtualMachineMigrationEnabled": true,
"VirtualMachineMigrationPerformanceOption": 2,
"VirtualMachineMigrationAuthenticationType": 1,
"MaximumVirtualMachineMigrations": 2,
"MaximumStorageMigrations": 2
}
},
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
to4kawa
Ultra Champion
04-20-2020
03:20 AM
props.conf
[adm_compute_qcheck]
INDEXED_EXTRACTIONS = JSON
JSON_TRIM_BRACES_IN_ARRAY_NAMES = true
KV_MODE = none
please add your setting.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
javiergn
Super Champion
04-20-2020
02:48 AM
Hi,
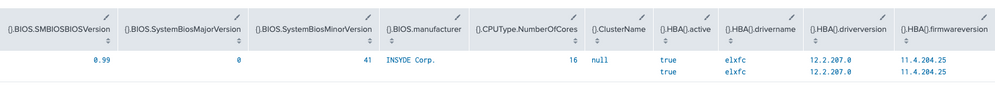
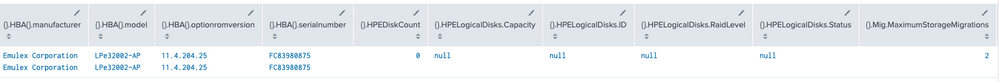
Running spath against the JSON block you included here seems to extract everything:
| makeresults
| eval myJSON = "
[
{
\"BIOS\": {
\"manufacturer\": \"INSYDE Corp.\",
\"SystemBiosMajorVersion\": 0,
\"SystemBiosMinorVersion\": 41,
\"SMBIOSBIOSVersion\": \"0.99\"
}
},
{
\"Checkpoint\": {
}
},
{
\"ClusterName\": null
},
{
\"CPUType\": {
\"NumberOfCores\": 16
}
},
{
\"HBA\": [
{
\"active\": true,
\"drivername\": \"elxfc\",
\"driverversion\": \"12.2.207.0\",
\"firmwareversion\": \"11.4.204.25\",
\"optionromversion\": \"11.4.204.25\",
\"manufacturer\": \"Emulex Corporation\",
\"model\": \"LPe32002-AP\",
\"serialnumber\": \"FC83980875\"
},
{
\"active\": true,
\"drivername\": \"elxfc\",
\"driverversion\": \"12.2.207.0\",
\"firmwareversion\": \"11.4.204.25\",
\"optionromversion\": \"11.4.204.25\",
\"manufacturer\": \"Emulex Corporation\",
\"model\": \"LPe32002-AP\",
\"serialnumber\": \"FC83980875\"
}
]
},
{
\"HPE\": [
]
},
{
\"HPEDiskCount\": 0
},
{
\"HPELogicalDisks\": {
\"Status\": null,
\"RaidLevel\": null,
\"ID\": null,
\"Capacity\": null
}
},
{
\"HPEPhysicalDisks\": [
]
},
{
\"Mig\": {
\"VirtualMachineMigrationEnabled\": true,
\"VirtualMachineMigrationPerformanceOption\": 2,
\"VirtualMachineMigrationAuthenticationType\": 1,
\"MaximumVirtualMachineMigrations\": 2,
\"MaximumStorageMigrations\": 2
}
},
]
"
| spath input=myJSON
| fields - myJSON, _time
Output:
Can you give us an example of a field that Splunk is not making available and the SPL you are using?
Get Updates on the Splunk Community!
Stay Connected: Your Guide to May Tech Talks, Office Hours, and Webinars!
Take a look below to explore our upcoming Community Office Hours, Tech Talks, and Webinars this month. This ...
They're back! Join the SplunkTrust and MVP at .conf24
With our highly anticipated annual conference, .conf, comes the fez-wearers you can trust! The SplunkTrust, as ...
Enterprise Security Content Update (ESCU) | New Releases
Last month, the Splunk Threat Research Team had two releases of new security content via the Enterprise ...