- Splunk Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Only show null values from timechart values(source...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
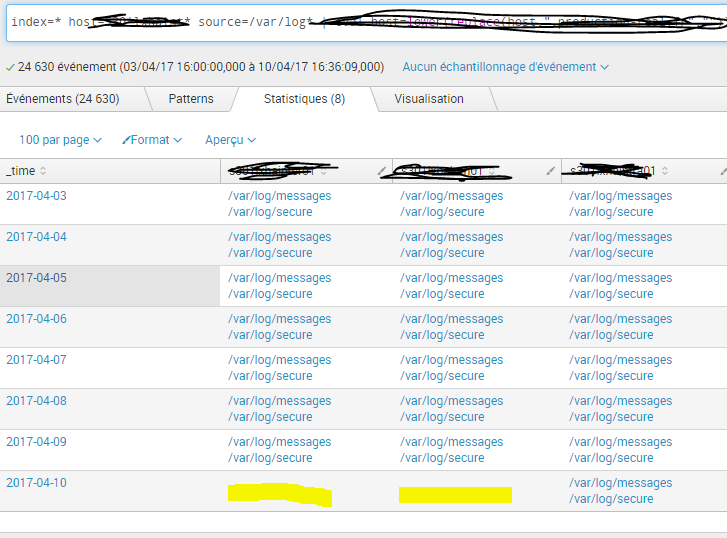
Hello guys,
could you tell me how to only show null cells from this kind of table, for alerting purpose?
Search: index=* host=XXX source=/var/log* | eval ... | timechart span=1d values(source) by host
Thanks.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I would setup alert based on this search
index= host=XXX source=/var/log | eval ... | timechart span=1d values(source) by host
| eval shouldAlert=0 | foreach * [eval shouldAlert=shouldAlert+if(isnull('<<FIELD>>') OR '<<FIELD>>'="",1,0) ]
| where shouldAlert>0
Basically it'll loop through all columns for a row and add 1 to shouldAlert field if there are null value in that rows. Later we only select rows where alert should be raised. You can then setup alert with condition 'if number of events greater than 0'
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Just add this to the end:
| eval NULLVALUE="NO"
| foreach * [eval NULLVALUE=if(isnull(<<FIELD>>), "YES", NULLVALUE)]
| search NULLVALUE="YES"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
No result... I tried src, host or even source for <>
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
No, you do not need to change ANYTHING. Type it in EXACTLY as I had it and it will work.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I would setup alert based on this search
index= host=XXX source=/var/log | eval ... | timechart span=1d values(source) by host
| eval shouldAlert=0 | foreach * [eval shouldAlert=shouldAlert+if(isnull('<<FIELD>>') OR '<<FIELD>>'="",1,0) ]
| where shouldAlert>0
Basically it'll loop through all columns for a row and add 1 to shouldAlert field if there are null value in that rows. Later we only select rows where alert should be raised. You can then setup alert with condition 'if number of events greater than 0'
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Same, no result... I tried src, host or even source for <>
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
YOu need to use literally '<>' there. No need to replace it with any field names.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks a lot!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
| where isnull(myfieldname)
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It doesn't work, I tried values(source) as src then use | where isnull(src) but nothing changed...
| where isnull(values(source)) = 'values' function is unsupported