Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Splunk Search
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- Splunk Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Re: How to use Foreach using multiple columns?
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
D2SI
Communicator
06-22-2018
04:21 AM
Hello there,
I am having a hard time figuring out how to use / how is working foreach + eval.
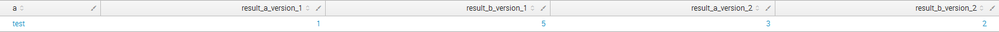
I have something like :
Which can be obtained using this search:
| makeresults
| eval a="test"
| eval result_a_version_1=1
| eval result_a_version_2=3
| eval result_b_version_1=5
| eval result_b_version_2=2
| fields - _time
| table a result_a_version_1 result_b_version_1 result_a_version_2 result_b_version_2
And I am trying to use foreach/eval to get this :
Matching search :
| makeresults
| eval a="test"
| eval result_a_version_1=1
| eval result_a_version_2=3
| eval result_b_version_1=5
| eval result_b_version_2=2
| fields - _time
| eval tota_a_b_version_1=result_a_version_1+result_b_version_1
| eval tota_a_b_version_2=result_a_version_2+result_b_version_2
| table a result_a_version_1 result_b_version_1 tota_a_b_version_1 result_a_version_2 result_b_version_2 tota_a_b_version_2
As the version number can vary, I am guessing I have to use foreach somehow.
Thanks in advance for any tip!
1 Solution
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
kamlesh_vaghela

SplunkTrust
06-22-2018
05:20 AM
Hi @D2SI,
I'm able to total of similar version. Can you please try the following search. I'm still working on the field name.
| makeresults
| eval test="test"
| eval result_a_version_1=1
| eval result_a_version_2=3
| eval result_b_version_1=5
| eval result_b_version_2=2
| eval result_a_version_3=50
| eval result_b_version_3=20
| fields - _time
| table test result_a_version_1 result_b_version_1 result_a_version_2 result_b_version_2 result_a_version_3 result_b_version_3
| foreach result_*_version_*
[ eval total_of_version_<<MATCHSEG2>>=if(isnotnull(total_of_version_<<MATCHSEG2>>),total_of_version_<<MATCHSEG2>>+'<<FIELD>>','<<FIELD>>') ]
Thanks
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
kamlesh_vaghela

SplunkTrust
06-22-2018
05:20 AM
Hi @D2SI,
I'm able to total of similar version. Can you please try the following search. I'm still working on the field name.
| makeresults
| eval test="test"
| eval result_a_version_1=1
| eval result_a_version_2=3
| eval result_b_version_1=5
| eval result_b_version_2=2
| eval result_a_version_3=50
| eval result_b_version_3=20
| fields - _time
| table test result_a_version_1 result_b_version_1 result_a_version_2 result_b_version_2 result_a_version_3 result_b_version_3
| foreach result_*_version_*
[ eval total_of_version_<<MATCHSEG2>>=if(isnotnull(total_of_version_<<MATCHSEG2>>),total_of_version_<<MATCHSEG2>>+'<<FIELD>>','<<FIELD>>') ]
Thanks
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
D2SI
Communicator
06-22-2018
07:46 AM
Seems to be what I was after using MATCHSEG2, thanks a lot !
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
kamlesh_vaghela

SplunkTrust
06-22-2018
07:55 AM
Glad to help you.
Happy Splunking
Get Updates on the Splunk Community!
More Ways To Control Your Costs With Archived Metrics | Register for Tech Talk
Tuesday, May 14, 2024 | 11AM PT / 2PM ET
Register to Attend
Join us for this Tech Talk and learn how to ...
.conf24 | Personalize your .conf experience with Learning Paths!
Personalize your .conf24 Experience
Learning paths allow you to level up your skill sets and dive deeper ...
Threat Hunting Unlocked: How to Uplevel Your Threat Hunting With the PEAK Framework ...
WATCH NOWAs AI starts tackling low level alerts, it's more critical than ever to uplevel your threat hunting ...