- Splunk Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Re: How to create a timechart for indexes with Cis...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
So I was trying to create an alert for blocked Cisco ASA traffic when there is an increase of 50% or more in today's traffic, compared to the daily average for the past 30 days. Found the example/answer here:
https://answers.splunk.com/answers/6789/avg-of-number-of-events-by-day.html
So I modified it to fit my scenario like this....
index=MyIndex1 sourcetype="cisco:asa" action="blocked" earliest=-30d@d latest=now | timechart span=1d count | stats last(count) as today_count avg(count) as avg_count | eval WarningAvgCount = (avg_count*1.5) | eval range=if(today_count>WarningAvgCount, "red", "green"). Add the | where range=red and viola, you have the alert.
results example
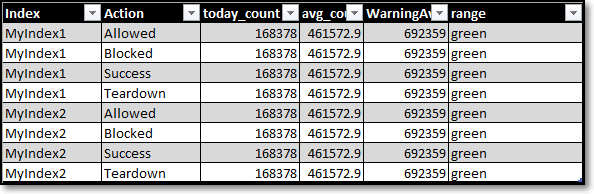
This sparked an idea: what if I included all of my indexes that have Cisco ASA data and had rows for each index and each of the actions (allowed, blocked, teardown, success)? This would keep me from making 4x panels for each of the indexes I have Cisco ASA data going into. I have tried several modifications without success. Appreciate the assistance in advance....
desired results theorized, as I do not have it working yet.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Give this a try
(index=MyIndex1 OR index=MyIndex2....all indexes here...) sourcetype="cisco:asa" action="*" earliest=-30d@d latest=now
| bucket span=1d _time | stats count by _time index action
| eval today_count=if(_time=relative_time(now(),"@d"),count,"null")
| stats max(today_count) as today_count avg(count) as avg_count by index action | eval WarningAvgCount = (avg_count*1.5) | eval range=if(today_count>WarningAvgCount, "red", "green") | where range=red
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Give this a try
(index=MyIndex1 OR index=MyIndex2....all indexes here...) sourcetype="cisco:asa" action="*" earliest=-30d@d latest=now
| bucket span=1d _time | stats count by _time index action
| eval today_count=if(_time=relative_time(now(),"@d"),count,"null")
| stats max(today_count) as today_count avg(count) as avg_count by index action | eval WarningAvgCount = (avg_count*1.5) | eval range=if(today_count>WarningAvgCount, "red", "green") | where range=red
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Worked beautifully!