- Splunk Answers
- :
- Splunk Administration
- :
- Getting Data In
- :
- Re: Why am I seeing a mismatch between Key-Value a...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
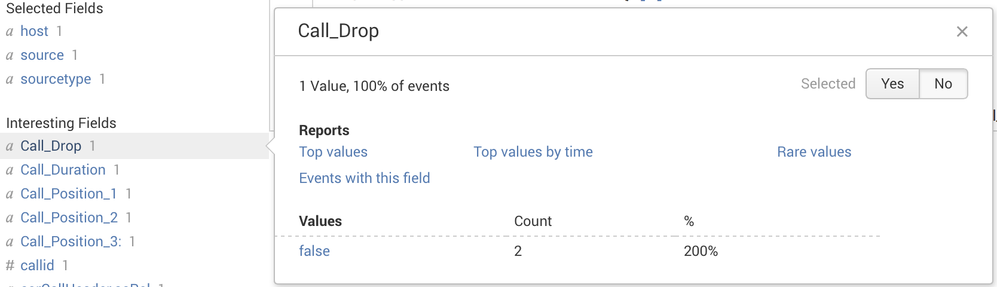
I have ingested JSON data & Splunk has extracted important fields automatically, but I see some mismatch between Key-Value & Count. There are many such fields with mismatch in count.
As per my screenshot for a single event, "Count" should be 1 instead of 2. Could someone advise me how to fix this problem.
(i don't see any problem with host, source, sourcetype)
props.conf
[json]
KV_MODE = json
INDEXED_EXTRACTIONS = JSON
TRUNCATE = 0
TIME_PREFIX = startTime":
MAX_TIMESTAMP_LOOKAHEAD = 16
SHOULD_LINEMERGE = False
NO_BINARY_CHECK = 0
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Set KV_MODE = none and your issue should go away.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Here is an event. Important fields have been extracted by Splunk. e.g corCallHeader.firstCellId=1.
Then I have used Alias to change it to Cell_ID.
{"corCallHeader":{"traceId":123456789123456,"startTime":1395736409790,"stopTime":1395736414180,"callDuration":4390,"rnti":0,"imsi":48,"tmsi":962442424,"
P.S - deleting original log
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I'd say your event contains two Call_Drop values.
If not, you could post anonymized events.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Can you post some sample entries?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Unfortunately, I can't share that data. Would you like to see any config?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If you can mask all the sensitive data, that should do. I'm interested in seeing the format of jSON with the mentioned field. On cursory look, the configuration looks correct. One question though, is this a custom sourcetype? and if yes, could you try renaming it to something else?