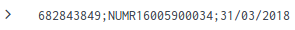- Splunk Answers
- :
- Splunk Administration
- :
- Getting Data In
- :
- Problem with display anonymised values in splunk w...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Problem with display anonymised values in splunk with SEDCMD :
Hello community,
I am trying to anonymise Data in Splunk, For that purpose I am using SEDCMD in splunk , The transformation applies perfectly with the _raw field ,but the fields are not modified accordingly.Please note that I do use csv extraction. Can U help ?
In my props.conf .Here's my command :
SEDCMD-NUMR_TICK = s/(SAV-xDSL)([0-9]{5})([0-9]{5})/NUMR1\3\2/g
My output is "which is correct" :
But when showing events I have my data shown without being anonymised :
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sounds like the indexed extractions take place before SEDCMD modifies the raw event. So you would need to write a TRANSFORMS command in props/transforms to perform the same translation on the field. If I'm not mistaken, that should work as follows.
props.conf
TRANSFORMS-NUMR_TICK = NUMR_TICK
transforms.conf
[NUMR_TICK]
SOURCE_KEY = field:NUMR_TICK
REGEX = (SAV-xDSL)([0-9]{5})([0-9]{5})
FORMAT = NUMR_TICK::NUMR1$3$2
WRITE_META = true
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello FrankVl ,
Thank you for your reply , I have followed your indications, It has solved my problem partially but not totally because now I have an output with multiple values NUMR_TICK :
NUMR_TICK SAV-xDSL0003460059
NUMR16005900034
This is my new configuration :
[NUMR_TICK]
FORMAT = NUMR_TICK::NUMRERIC1$3$2
MV_ADD = 0
REGEX = (SAV-xDSL)([0-9]{5})([0-9]{5})
SOURCE_KEY = field:NUMR_TICK
WRITE_META = true
I have added MV_ADD to avoid that behavior.But I've got no results.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
MV_ADD is only valid for search time extractions.
There is something in the docs about using $0 at the start of the FORMAT string: FORMAT = $0 NUMR_TICK::NUMRERIC1$3$2
But I don't fully understand what effect that would have (but perhaps worth a try). I've never done this myself, so you may need to wait for someone else to come by this question to help you further.