- Apps and Add-ons
- :
- All Apps and Add-ons
- :
- Trigger conditions to get the splunk alert if perc...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
HI,
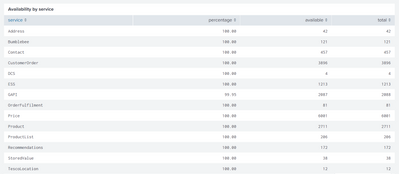
I am using the below query to calculate the percentage value for available and total columns.
index=nextgen mango_trace="SyntheticTitan*" | where status = "200" OR status = "204"|stats count as available by service | appendcols [search index=nextgen mango_trace="SyntheticTitan*" | stats count as total by service] | eval percentage = round((available/total)*100,2) |table service, percentage, available, total
I wanted to trigger an alert when the percentage values are less than 100.00. My Splunk search results for the above query looks like
Can you please help me with the trigger conditions to set an alert of any of the service percentages is < than 100.00
Thanks,
SG
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @SG,
I agree with @ITWhisperer, why don't you trigger the alert when your status is different than 200 or 204?
Anyway, following your login, you have only to add a final condition using "where" command:
index=nextgen mango_trace="SyntheticTitan*"
| where status = "200" OR status = "204"
| stats count as available by service
| appendcols [ search
index=nextgen mango_trace="SyntheticTitan*"
| stats count as total by service
]
| eval percentage = round((available/total)*100,2)
| table service percentage available total
| where percentage<100In addition, it isn't a best practice to use the search command after the main search, your search is slower and you don't need to use appendcols also because there's the limit of 50,000 results in subsearches.
So please, try something like this.
index=nextgen mango_trace="SyntheticTitan*"
| stats count(eval(status="200")) AS type_200 count(eval(status="204")) AS type_204 count AS total by service
| eval percentage=round(((type_200+type_204)/total)*100,2)
| table service percentage available total
| where percentage<100Ciao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @SG,
I agree with @ITWhisperer, why don't you trigger the alert when your status is different than 200 or 204?
Anyway, following your login, you have only to add a final condition using "where" command:
index=nextgen mango_trace="SyntheticTitan*"
| where status = "200" OR status = "204"
| stats count as available by service
| appendcols [ search
index=nextgen mango_trace="SyntheticTitan*"
| stats count as total by service
]
| eval percentage = round((available/total)*100,2)
| table service percentage available total
| where percentage<100In addition, it isn't a best practice to use the search command after the main search, your search is slower and you don't need to use appendcols also because there's the limit of 50,000 results in subsearches.
So please, try something like this.
index=nextgen mango_trace="SyntheticTitan*"
| stats count(eval(status="200")) AS type_200 count(eval(status="204")) AS type_204 count AS total by service
| eval percentage=round(((type_200+type_204)/total)*100,2)
| table service percentage available total
| where percentage<100Ciao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for the solution. I updated the query as suggested.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @SG,
good for you, see next time.
Ciao and happy splunking.
Giuseppe
P.S.: Karma Points are appreciated by all the Contributors 😉
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Why not simply trigger when status is not equal to 200 or 204?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
HI, I wanted to see the percentage of outages for each service.