- Splunk Answers
- :
- Using Splunk
- :
- Alerting
- :
- Re: How to set alert schedule?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How to set alert schedule?
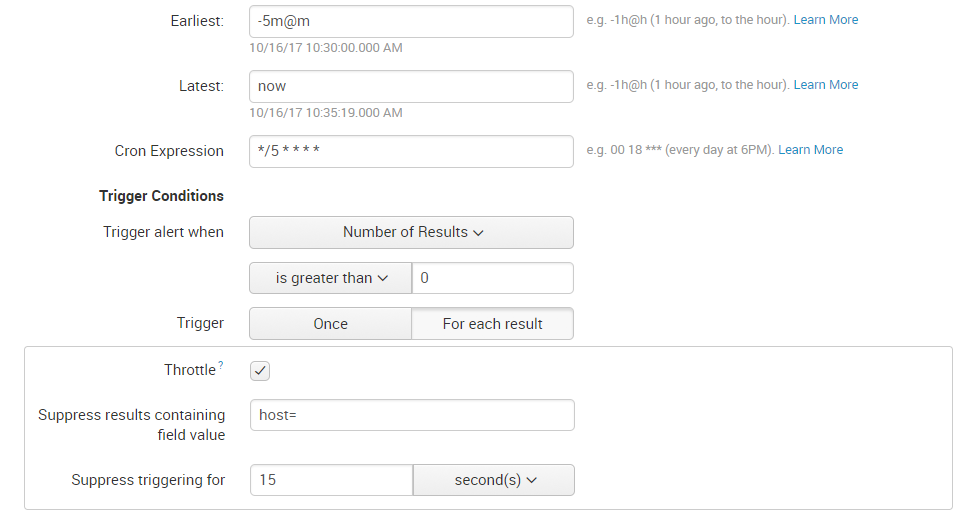
We have 15 different hosts, we enabled an alert with condition "if host is down we need to alert it".
It has to check every 5 min if any host is down. It has to alert it and also should not alert for second time for same host. How should I do it?
example: At 10:00 AM HostA is down we need to alert it and if at 10:01 HostA and HostB are down then I should get an alert saying HOSTB is down, but I should not receive alert for HOSTA again for 15mins.
Here is what we did, is it correct?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You are using correct option. Throttle option will ensure alert is not generated again for same host. Only thing you may want to change is you need to put name of the field without equals sign. i.e. host
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
saifuddin, you can try in this way by loading up all the required host into a look up and append/join/lookup with the actual query for the host count(whcih represents host up or down) OR a particular message which lets you know host is down.
| inputlookup listof_hosts_alerts.csv
| append [search index= host=host*
| stats count by host]
| stats values(count) AS count by host
| fillnull value=0
| eval status=case(count>0,"Up", count=0, "Down", 1=1, UNKNOWN)
| fields - count
| search status=Down