- Splunk Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Re: Why is my tstats including other counts?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
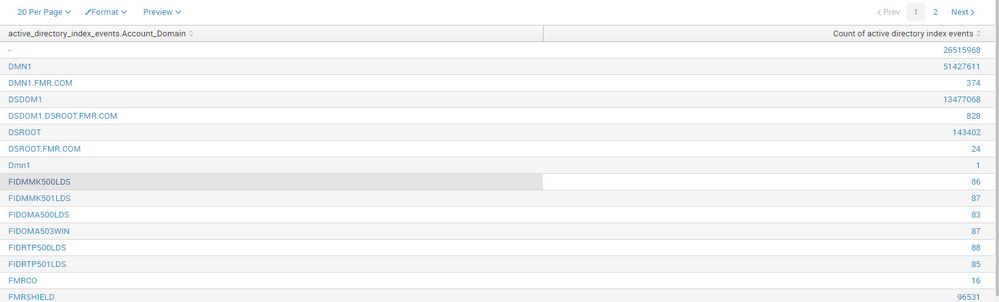
I am querying an accelerated data model for active directory, using the search below. However, the results are showing domains that are not being requested. Can someone explain this to me?
Search:
|tstats count AS "Count of active directory index events" from datamodel=Active_Directory where (nodename = active_directory_index_events) (active_directory_index_events.Account_Domain="DMN1" OR active_directory_index_events.Account_Domain="DSDOM1" OR active_directory_index_events.Account_Domain="WINROOT" OR active_directory_index_events.Account_Domain="DSROOT" OR active_directory_index_events.Account_Domain="VC1ROOT" OR active_directory_index_events.Account_Domain="VC2ROOT" OR active_directory_index_events.Account_Domain="VC3ROOT" OR active_directory_index_events.Account_Domain="FMRSHIELD") BY active_directory_index_events.Account_Domain
Results:
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
My suspicion is that the raw events that fed the model have "Account Domain" as a multi-valued field. The summary includes a snapshot of the event with each value of the multi-value field captured in amber. When you search, the WHERE tags the summary event, and the BY then splits out those multi-values each into their own row. I saw this a lot with some (incorrectly ingested) JSON using INDEXED_EXTRACTIONS (which behaves a bit like data model summaries).
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
My suspicion is that the raw events that fed the model have "Account Domain" as a multi-valued field. The summary includes a snapshot of the event with each value of the multi-value field captured in amber. When you search, the WHERE tags the summary event, and the BY then splits out those multi-values each into their own row. I saw this a lot with some (incorrectly ingested) JSON using INDEXED_EXTRACTIONS (which behaves a bit like data model summaries).
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks. That does appear to be the case... back to the drawing board....
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Note that you might be able to post-filter. The events that matched your search end up having two domains mentioned. If it's mentioned in a way that matches your original search criteria (that is, it's not producing a false positive), then all you'd have to do is re-filter. I'd suggest a macro with just "field=value1 or field=value2" that you can place in both the initial part (the tstats call) and the subsequent | search so that the lists can be easily kept in sync.