- Splunk Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Sum of new events over time
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi all!
I'm new to Splunk and I'm having trouble making my search correct.
I've tried searching but found no case exactly like mine.
the problem:
I have a log with many 'Events', each event has a status: New/Old.
Old means it has been dealt with.
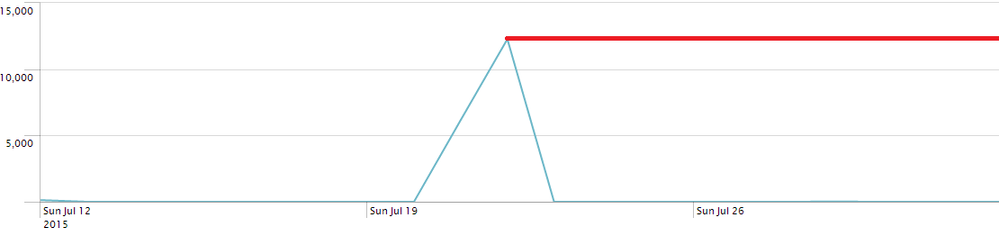
I would like to make a line-chart that will show the total number of new events over time.
My chart:
The way the chart should look:
This is what I've tried so far:
host="MyHost" Status="New" | timechart count(Status)
... | timechart sum(Status)
... | timechart sum(count(Status))
Any help will be appreciated!
Thanks!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This should do what you need:
host="MyHost" Status="New" | timechart count | accum count
That will turn the count per timeslot into a running total.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This should do what you need:
host="MyHost" Status="New" | timechart count | accum count
That will turn the count per timeslot into a running total.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you!
That worked!