- Splunk Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Re: timechart by count, average(timetaken) by type
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
timechart by count, average(timetaken) by type
Hi,
i have data like below
Type count timeTakenToexceute time
abc 2 2 sec 09-01-2016, 09-02-2016
xyz 1 1 sec 09-01-2016
needed timechart based on day, i am trying like below but missing count
..... | timechart span=1d avg(timetaken) by type
please help
thanks in advance.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Try like this. It will create fields like AvgTime :Type and Count :Type. E.g. AvgTime :abc, Count: xyz
..... | timechart span=1d avg(timetaken) as AvgTime count as Count by type
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Both Average and count fields are different entity and can possibly have different magnitude in the y-axis. Why do you want to merge both? do you want to merge both average and count for each type? If yes, then just remove by type in the above query.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Try this
... | bin span=1d _time | stats avg(timetaken) as average count by _time typ
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
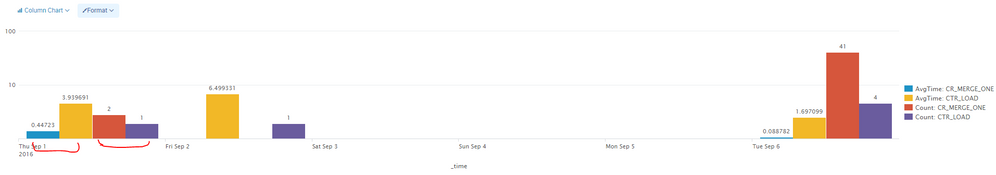
Thank you for your answers, but the issue i am facing here for count its showing separate bar, but i need both average and count displaying in single bar, is it possible.
please find the below image, first two bars shows average time taken and second two bars shows count of each type, i want there four bars in two bars displaying average and count.
thanks in advance
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Have you tried stacked chart?
https://docs.splunk.com/Splexicon:Stackmode
OR, overlay may be a better option