- Splunk Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- auto increment on query
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
auto increment on query
Hello,
I'am writing a query to retrieve comments of my clients
This is my query
| eval q_commentaireSupplementaire= "Comm:".q_commentaireSupplementaire
my result :
What i want is to have an auto increment =>
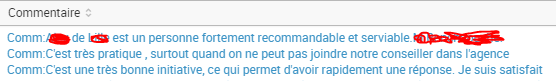
Comm 1:**** de *** est un personne fortement recommandable et serviable.** ****.
Comm 2:C'est très pratique , surtout quand on ne peut pas joindre notre conseiller dans l'agence
Comm 3:C'est une très bonne initiative, ce qui permet d'avoir rapidement une réponse. Je suis satisfait
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Try this:
... | streamstats count as row | eval q_commentaireSupplementaire= "Comm " . row . ":" . q_commentaireSupplementaire
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
i add the count ,and then the counter ,i still have a prolem with sorting
Comm 11:...
Comm 1:...
Comm 15:...
I used aldo sort desc and asc ,but doesnt work too
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@taha13, add printf() function after streamstats to pad zeros to row count values as sorting is considering the Column as string. The following pads upto three zeros i.e. can sort up to 999 comments.
| streamstats count as row
| eval sno=printf("%03d",row)
Also make sure that the field is not multivalue rather it is single value. You can share your current query if this does not help.
| makeresults | eval message= "Happy Splunking!!!"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@niketnilay
Error in 'eval' command: The 'printf' function is unsupported or undefined.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
| streamstats count as row
| eval sno =printf("%03d",row)
| eval q_commentaireSupplementaire= "Comm ".sno.": ".q_commentaireSupplementaire
| stats VALUES(q_commentaireSupplementaire) AS Commentaire BY qa_noteSatisfaction
| sort qa_noteSatisfaction desc
| rename qa_noteSatisfaction AS Note_Satisfaction
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@taha, which version of Splunk are you on?
instead of printf() use the following eval with case()
| eval sno=case(len(sno)=1,"00".sno,len(sno)=2,"0".sno,true(),sno)
Also, just to be sure of what your data looks like, I was interested in transforming command before streamstats, that you have posted. Post that piece of search if above eval with case() does not work.
| makeresults | eval message= "Happy Splunking!!!"