- Splunk Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Re: What's wrong with this case statement?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
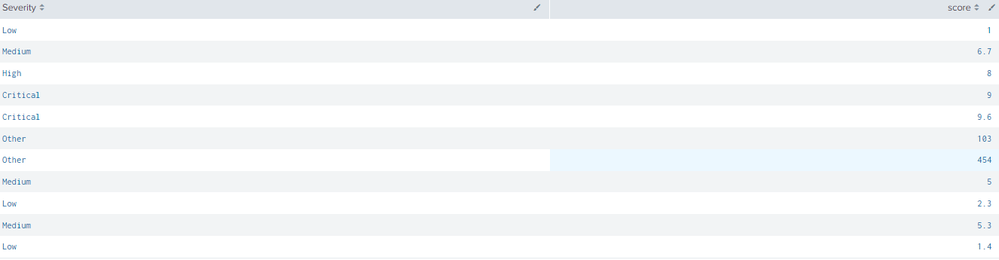
What's wrong with this case statement?
When I add this case statement to my search, all results for Severity are "Other". What did I miss?
| eval Severity=case(score>=0.1 AND score<=3.9, "Low", score>=4.0 AND score<=6.9, "Medium", score>=7.0 AND score<=8.9, "High", score>=9.0 AND score<=10.0, "Critical", true(), "Other")- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Solved! Thank you to everyone that provided hints - it turns out that the field in question was coming from a lookup, and for some reason I could not successfully apply the case statement in my query. But I opened up the lookup query, added the case statement there, and it worked. I don't understand why this worked, but it did.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
but I used your query and it worked correctly:
its possible that your score filed is multivalue field like my query:
| makeresults
| eval temp="1 6.7 8 9 9.6 103 454 5 2.3 5.3 1.4"
| eval score=split(temp," ")
| fields - temp,_time
| mvexpand score
| eval Severity=case(score>=0.1 AND score<=3.9, "Low", score>=4.0 AND score<=6.9, "Medium", score>=7.0 AND score<=8.9, "High", score>=9.0 AND score<=10.0, "Critical", true(), "Other")
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, it does seem to work with your query but unfortunately it does not work in mine. I have confirmed the field is not multivalue.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If your fields which contain "numbers" misbehave it's often the case of the fields being in fact string representations of numbers. Try eval-ing the field before your case to a number using
| eval score=tonumber(score)
Oh, and assuming all your scores are non-negative, you can limit your number of conditions since they are evaluated left to right until a match is found. So if the first condition (0.1 - 3.9) evaluates to false, there is no point of requiring the number to be at least 4.0 in the next step because if it was smaller, it would have matched the first condition.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you for this - I did verify that the field was a number, but I plugged in your eval anyway. Still doesn't work, though I appreciate the tip about reading from left to right (I didn't know that).
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
In verbose mode you can check the type of field from selected/interesting field columns. If before the field name is # => number and if it's a => character. This is the easiest way to see that.
r. Ismo
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
That is a good tip - yes, the field is a number.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @mistydennis ,
sometimes I found problems in dots management, so I hint to try this:
| eval Severity=case(score>0 AND score<4, "Low", score>=4 AND score<7, "Medium", score>=7 AND score<9, "High", score>=9 AND score<=10, "Critical", true(), "Other")Ciao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I tried this as well, no luck. All values are still "Other".
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
One way to see what those fields contains is a create a new field like
...
| eval contains=">" . field . "<"
| ...That way it's not needed to guess what that field contains.