- Splunk Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- REGEX HELPING PLEASE
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
REGEX HELPING PLEASE
struggling to extract underlined items as RUN NAME
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Simple regex:
| rex “\"run\.name\"\:\"(?<runname>[^\"]+)”
run.name will be extracted to runname field.
If this helps, give a like below.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This should do the trick, thi
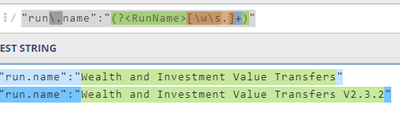
| rex field=_raw "run\.name":"(?<RunName>[\w\s.]+)"
The named capture group doesn't like the space but you can use the "| rename RunName AS "Run Name" "
http://regex101.com is where I do most of my testing
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
does it work the same for below extract? cause im not getting it, also tried it on regex101
------------------------------------------------------------------------------------------------------------------------------------
2020-08-11 14:29:42,212 [8618-12939] ERROR NodePoolServiceImpl - [urn:uuid:979ECCA3B9BACEB335159714896138959] Find and lock (capabilities : [{"extra.executor.id":{"host.name":"https://spbbwfapp1v.standardbank.co.za:8443","context.path":"/workfusion","task.uuid":"f6bb5671-b4c3-4917-bd02-01e23488a9f6","run.name":"Business Banking AO and Sales 2020/08/11","run.uuid":"9c1d82a7-16e2-4362-9a5d-404d2b694b7d","run.author.fullname":"Mark Erasmus","run.author.email":"Mark.Erasmus@standardbank.co.za","task.name":"ia-process-business-banking-ao v2.0.3 (UpdateCompanyDataRobot)"},"browserName":"chrome","javascriptEnabled":true,"maximize.on.startup":true,"chromeOptions":{"args":[],"extensionFiles":[],"extensions":[],"experimentalOptions":{},"capabilities":{"caps":{}}},"platform":"WINDOWS"}]) failed with message : [urn:uuid:979ECCA3B9BACEB335159714896138959] Can not find any free node with requested capabilities [{"extra.executor.id":{"host.name":"https://spbbwfapp1v.standardbank.co.za:8443","context.path":"/workfusion","task.uuid":"f6bb5671-b4c3-4917-bd02-01e23488a9f6","run.name":"Business Banking AO and Sales 2020/08/11","run.uuid":"9c1d82a7-16e2-4362-9a5d-404d2b694b7d","run.author.fullnam
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
My bad forgot to escape the double quotes for splunk. the section in the square brackets with catch a-zA-Z0-9 backslash and forward slash. If there are other characters $,%,- etc.. in the field they will need added
| rex field=_raw "\"run\.name\":\"(?<RunName>[\w\\\\/\s]+)\","