- Splunk Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Re: Kafka regex: Why is the command not working in...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
{"topic": "amx", "total_lag": 2670, "partitions": [{"lag": 117, "partition_number": 0}, {"lag": 122, "partition_number": 1}, {"lag": 130, "partition_number": 2}, {"lag": 130, "partition_number": 3}, {"lag": 148, "partition_number": 4}, {"lag": 144, "partition_number": 5}, {"lag": 158, "partition_number": 6}, {"lag": 130, "partition_number": 7}, {"lag": 123, "partition_number": 8}, {"lag": 145, "partition_number": 9}, {"lag": 130, "partition_number": 10}, {"lag": 127, "partition_number": 11}, {"lag": 123, "partition_number": 12}, {"lag": 121, "partition_number": 13}, {"lag": 118, "partition_number": 14}, {"lag": 125, "partition_number": 15}, {"lag": 133, "partition_number": 16}, {"lag": 161, "partition_number": 17}, {"lag": 134, "partition_number": 18}, {"lag": 151, "partition_number": 19}]}
index=orion-platform source="/opt/bda/logs/kafkalag.log" |spath output=AA path=counterList{1} | rex field=AA "\"lag\":\s(?.\w+)\,\s\"partition_number\"\:\s(?\d+)\}" max_match=100 | table State1,partition_number
Above command not working in splunk search.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi
Can you please try the following search? I haven't used any regular expression but it will give you all the data from JSON event.
YOUR_SEARCH |
| rename partitions{}.lag as lag, partitions{}.partition_number as partition_number
| eval temp = mvzip(lag,partition_number) | stats count by _time total_lag,topic,temp
| eval lag = mvindex(split(temp,","),0) ,partition_number=mvindex(split(temp,","),1) | table topic total_lag lag partition_number
My Sample Search:
| makeresults
| eval _raw="{\"topic\": \"amx\", \"total_lag\": 2670, \"partitions\": [{\"lag\": 117, \"partition_number\": 0}, {\"lag\": 122, \"partition_number\": 1}, {\"lag\": 130, \"partition_number\": 2}, {\"lag\": 130, \"partition_number\": 3}, {\"lag\": 148, \"partition_number\": 4}, {\"lag\": 144, \"partition_number\": 5}, {\"lag\": 158, \"partition_number\": 6}, {\"lag\": 130, \"partition_number\": 7}, {\"lag\": 123, \"partition_number\": 8}, {\"lag\": 145, \"partition_number\": 9}, {\"lag\": 130, \"partition_number\": 10}, {\"lag\": 127, \"partition_number\": 11}, {\"lag\": 123, \"partition_number\": 12}, {\"lag\": 121, \"partition_number\": 13}, {\"lag\": 118, \"partition_number\": 14}, {\"lag\": 125, \"partition_number\": 15}, {\"lag\": 133, \"partition_number\": 16}, {\"lag\": 161, \"partition_number\": 17}, {\"lag\": 134, \"partition_number\": 18}, {\"lag\": 151, \"partition_number\": 19}]}"
| kv
| rename partitions{}.lag as lag, partitions{}.partition_number as partition_number
| eval temp = mvzip(lag,partition_number) | stats count by _time total_lag,topic,temp
| eval lag = mvindex(split(temp,","),0) ,partition_number=mvindex(split(temp,","),1) | table topic total_lag lag partition_number
Please let me know if assistance required.
Thanks
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
HI @pswalia06,
Can you please try the following search?
YOUR_SEARCH
|kv
| rename partitions{}.lag as lag, partitions{}.partition_number as partition_number
| timechart latest(total_lag) as total_lag by topic
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Is there a way to convert this feed to a json format? It's pretty close....
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
it is json format only
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi
Can you please try the following search? I haven't used any regular expression but it will give you all the data from JSON event.
YOUR_SEARCH |
| rename partitions{}.lag as lag, partitions{}.partition_number as partition_number
| eval temp = mvzip(lag,partition_number) | stats count by _time total_lag,topic,temp
| eval lag = mvindex(split(temp,","),0) ,partition_number=mvindex(split(temp,","),1) | table topic total_lag lag partition_number
My Sample Search:
| makeresults
| eval _raw="{\"topic\": \"amx\", \"total_lag\": 2670, \"partitions\": [{\"lag\": 117, \"partition_number\": 0}, {\"lag\": 122, \"partition_number\": 1}, {\"lag\": 130, \"partition_number\": 2}, {\"lag\": 130, \"partition_number\": 3}, {\"lag\": 148, \"partition_number\": 4}, {\"lag\": 144, \"partition_number\": 5}, {\"lag\": 158, \"partition_number\": 6}, {\"lag\": 130, \"partition_number\": 7}, {\"lag\": 123, \"partition_number\": 8}, {\"lag\": 145, \"partition_number\": 9}, {\"lag\": 130, \"partition_number\": 10}, {\"lag\": 127, \"partition_number\": 11}, {\"lag\": 123, \"partition_number\": 12}, {\"lag\": 121, \"partition_number\": 13}, {\"lag\": 118, \"partition_number\": 14}, {\"lag\": 125, \"partition_number\": 15}, {\"lag\": 133, \"partition_number\": 16}, {\"lag\": 161, \"partition_number\": 17}, {\"lag\": 134, \"partition_number\": 18}, {\"lag\": 151, \"partition_number\": 19}]}"
| kv
| rename partitions{}.lag as lag, partitions{}.partition_number as partition_number
| eval temp = mvzip(lag,partition_number) | stats count by _time total_lag,topic,temp
| eval lag = mvindex(split(temp,","),0) ,partition_number=mvindex(split(temp,","),1) | table topic total_lag lag partition_number
Please let me know if assistance required.
Thanks
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
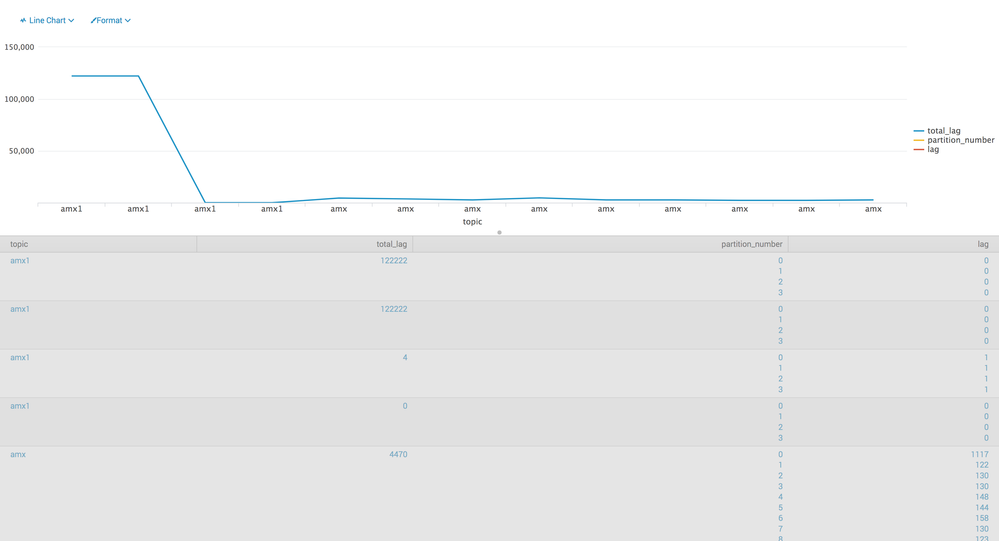
The amx value is showing continuesly and the total_lag is showing the same repeated value for each lag and partition_name
I want this
Topic_name total_lag partition_number lag
amx 240. 0. 20
1. 30
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@pswalia06
Are you looking for this?
| makeresults
| eval _raw="{\"topic\": \"amx\", \"total_lag\": 2670, \"partitions\": [{\"lag\": 117, \"partition_number\": 0}, {\"lag\": 122, \"partition_number\": 1}, {\"lag\": 130, \"partition_number\": 2}, {\"lag\": 130, \"partition_number\": 3}, {\"lag\": 148, \"partition_number\": 4}, {\"lag\": 144, \"partition_number\": 5}, {\"lag\": 158, \"partition_number\": 6}, {\"lag\": 130, \"partition_number\": 7}, {\"lag\": 123, \"partition_number\": 8}, {\"lag\": 145, \"partition_number\": 9}, {\"lag\": 130, \"partition_number\": 10}, {\"lag\": 127, \"partition_number\": 11}, {\"lag\": 123, \"partition_number\": 12}, {\"lag\": 121, \"partition_number\": 13}, {\"lag\": 118, \"partition_number\": 14}, {\"lag\": 125, \"partition_number\": 15}, {\"lag\": 133, \"partition_number\": 16}, {\"lag\": 161, \"partition_number\": 17}, {\"lag\": 134, \"partition_number\": 18}, {\"lag\": 151, \"partition_number\": 19}]}"
| kv
| rename partitions{}.lag as lag, partitions{}.partition_number as partition_number
| table topic total_lag partition_number lag