- Splunk Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Increase count of events but no field results show...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Increase count of events but no field results show up
When searching with this sample query, results show up like below
index=abc sourcetype=def 1.1.1.1
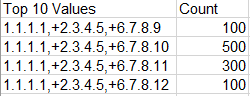
For example, field1 has the following values:
field2:
Since each IP needs to be displayed, I wrote this query:
|eval temp=split(field1,",+") | eval IP1=mvindex(temp,0) | eval IP2=mvindex(temp,1) | eval IP3=mvindex(temp,2)
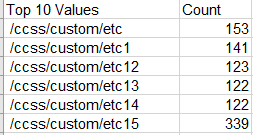
But there's also a requirement to search for total events >= 1000 and still able to display the 3 IPs in a table along with values(field2). When I use count >= 5, results are displayed, but when I use count >= 1000, the results are not. For example: below is expected result
_time IP1 IP2 IP3 field2
4/8/2019 23:16 1.1.1.1 2.3.4.5 6.7.8.9 /ccss/custom/etc
/ccss/custom/etc1
4/8/2019 23:16 1.1.1.1 2.3.4.5 6.7.8.10 /ccss/custom/etc
/ccss/custom/etc2
4/8/2019 23:16 1.1.1.1 2.3.4.5 6.7.8.11 /ccss/custom/etc
/ccss/custom/etc3
This is my query so far:
index=abc sourcetype=def 1.1.1.1
|eval temp=split(field1,",+") | eval IP1=mvindex(temp,0) | eval IP2=mvindex(temp,1) | eval IP3=mvindex(temp,2)
| stats values(field2) as field2 count(field1) as event_count by IP1 IP2 IP3 _time | where event_count >=1000
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You may not be aware that all the *stats commands and functions are multivalue-aware/safe, so try this:
index=abc sourcetype=def 1.1.1.1
|eval IP=split(field1,",+")
| stats values(field2) AS field2 count(field1) AS event_count BY IP _time
| where event_count >=1000
I am skeptical that you need the _time there, but I am trusting you on that part. Perhaps this is more what you need?
index=abc sourcetype=def 1.1.1.1
|eval IP=split(field1,",+")
| stats count AS event_count BY IP field1
| stats list(*) AS * sum(event_count) AS total_event_count BY IP
| where total_event_count >=1000
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I still got the "No results found." message even though there are more than 1000 events found..When I lowered it to 5 I got some results.