- Splunk Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Re: How to find a user behind an action?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How to find a user behind an action?
Hi
I have a report showing who have added or removed a person to or from a group.
Like :
index="win*" (EventCode=4728 OR EventCode=4729)
| table _time, result, target_group, target_user, src_user
This however returns from time to time a user called "XXXXX01, XXXXX02 Etc, which is a shared account in our PAM solution. I can find the user behind by searching:
index="PAM" duser="XXXXX*" "cn2=(Action: Connect)"
| table _time, duser, suser, command, reason
How can i make the first search, then in case user = XXXXX01, search for the latest time XXXXX01 was used related to the time in the first search.
At the moment we need to run the search side by side, and the find the correct time and check out of the XXXXX account, since the ie XXXXX01 can be checked out many times during a work day.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @yuanliu
I do like your solution, but i do have a problem, since a lot of times when a user takes a administrative account, they do multible changes see below.
Your soultion only gives me 2 matches, which is the first action for the the user created
Sorry to be a pain ....
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
So, the use case will need an end condition that is not merely index=win*. Is there an action (event) that indicates a user returning ("check in"?) the admin user in PAM? According to your original description, in win* logs, you can only see the admin user. There is a small opportunity this information can be deduced from the next time the same admin user gets checked out by a different suser. But such deduction may not be accurate. Also, this method requires each suser data point to be used as both beginning and end. This is quite difficult for SPL.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
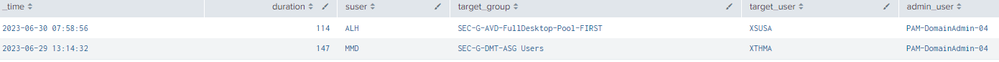
So what i would like to end up with is a table like:
_time (first search), action, target_group, target_user, src_user, suser
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The question leaves a lot to be clarified. First things first. The first search returns a src_user and a target_user; the second search involves a duser and an suser. Which user will have that value XXXXX01, XXXXX02, etc? I am guessing that is target_user in the first, and duser in the second. Is this correct? If so, suser must be "the user behind". Is this correct? Is there any relationship between this "user behind" and src_user? I will take the assumption of no relationship. In other words, src_user is just another idle data field like result in this use case. Meanwhile, I will assume that target_group is uniquely determined by target_user.
Secondly, what does "check out" mean in terms of data? Also, "search for the latest time" something happens is somewhat in conflict with something can happen "many times during a work day." How do you expect to resolve this conflict? I will pursue the latest time first.
Lastly, to "find the correct time" in both datasets, there has to be a relationship between the two. Which index is expected to have the matching event first? Or is the logic simply to assume two otherwise matching events in the two indices within a certain time interval are "the correct time"? I will take the logic of matching target_user in index=win* with duser in index=PAM within any +/- 1 minute interval on the calendar.
Using map, you can search for the latest event involving target_user of that name pattern in win* and search a corresponding duser event in between -1 minute and + 1 minute of that win* event.
index="win*" (EventCode=4728 OR EventCode=4729)
target_user=XXXXX*
| stats max(_time) as _time, latest(result) as result, latest(src_user) as src_user by target_group, target_user
| eval interval_start = _time - 60, interval_end = _time + 60
| map search="search index=PAM duser=$target_user$ \"cn2=(Action: Connect)\" earliest=$interval_start$ latest=$interval_end$"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @yuanliu
Thank you for your response, and I do agree some clarifycation is needed:
The overall is the following: To identify the user behind, when someone has been using the shared administrative accounts (XXXXX01, etc) to add or remove accounts from sensitive groups.
The work process is that a user, log on to our PAM solution as suser, they check out the admin user (duser), duser is then used to make changes to target_user/target_group.
First challenge is, that the time from the check out of XXXXX01 in the PAM solution to the actual change of the account is not fixed, it can be anywhere from 1 minute to an hour.
Second problem is that to different user can check out the same account, (one after the other, not at the same time)
I need src_user in the first search to match duser in second search. I need the time of the second search to be within the hour of the first search. ( I will accept that in rear cases this will give more than one suser account)
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you for the clarification. This is now much easier to conceptualize.
So, this is the pairing of events that begins with PAM and a duser of an admin account, and ends with win* where the source_user is that admin account. Looks like another job for transaction. Something like
(index="PAM" duser="XXXXX*" "cn2=(Action: Connect)") OR (index="win*" (EventCode=4728 OR EventCode=4729) source_user=XXXXX*)
| eval admin_user = coalesce(duser, source_user)
| transaction admin_user startswith=index=PAM endswith=win*
| table _time duration suser target_user admin_user ``` add any other fields of interest ```