- Splunk Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Re: Field extraction in a message
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
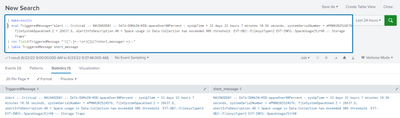
Hi Everyone,
I have a field called as TriggeredMessage coming in an event in Splunk and I want to extract the short description field from it. Below is the sample triggeredmessage and it will be varying :
Alert::Serious::Server::Memory Utilization is 92 %, which is above threshold 90% & less than 95%::memory.
And I want to extract a short description as below :
Server::Memory Utilization is 92 %, which is above threshold 90% & less than 95%
I am trying the regex but not working for me. Please help me on this.
Thanks.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Splunk4,
please try this:
| rex field=TriggeredMessage "^([^:]+..){2}(?<short_message>([^:]+..){2})"that you can test at https://regex101.com/r/bqgbhr/1
Ciao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Giuseppe's answer is more accurate. Thank you
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Splunk4,
please try this:
| rex field=TriggeredMessage "^([^:]+..){2}(?<short_message>([^:]+..){2})"that you can test at https://regex101.com/r/bqgbhr/1
Ciao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks,,It's working..i have just modified to below in order to remove the :: coming at the end
| rex field=TriggeredMessage "^([^:]+..){2}(?<short_message>([^:]+..){2})::"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Splunk4,
good for you, see next time!
Please accept one answer for the other people of Community
Ciao and happy splunking
Giuseppe
P.S.: Karma Points are appreciated by all the Contributors 😉
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @gcusello ,
In the aboce message, some messages can also come up with spaces in between like below :
Alert :: Serious :: Server :: Memory Utilization is 92 %, which is above threshold 90% & less than 95% :: memory
So can this regex modified in order to capture the messages with spaces as well?
Thanks
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Splunk4,
the above regex runs also with spaces, as you can test at the above link, infact the spaces are already considered in the group [^:]+
but anyway, you can test this regex:
| rex "^([^:]+::\s*){2}(?<short_message>([^:]+::){2})"Ciao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @gcusello ,
I tried the regex for one of below event but seems its not working.
Alert :: Critical :: NXUSWSDD01 :: DATA-DOMAIN-MIB:spaceOver90Percent : sysUpTime = 33 days 22 hours 7 minutes 10.56 seconds, systemSerialNumber = APM00202524576, fileSystemSpaceUsed.2 = 26637.6, alertInfoDescription.48 = Space usage in Data Collection has exceeded 90% threshold. EVT-OBJ::FilesysType=2 EVT-INFO::SpaceUsage(%)=90 :: Storage Traps
Thanks
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Splunk4,
ok, please try this:
| rex field=TriggeredMessage "^([^:]+::\s+){2}(?<short_message>.*)::"that you can test at https://regex101.com/r/bqgbhr/2
Ciao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
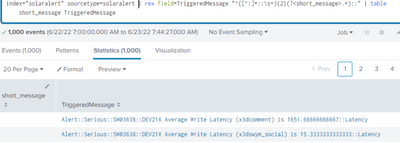
It is bringing only the server name(NXUSWSDD01) present at the third position in events with spaces and in events without spaces it is not bringing anything.
Thanks
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Splunk4,
are you sure to have exactly copied my regex?
because it's running in my pc:
Ciao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @gcusello ,
Below is the one which is showing blank for events without spaces :
Below is the one which is with spaces.It looks like some events are with special characters
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Splunk4 ,
ok, please try this:
| rex field=TriggeredMessage "^([^:]+::\s*){2}(?<short_message>.*)::"that you can test at https://regex101.com/r/bqgbhr/3
Ciao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
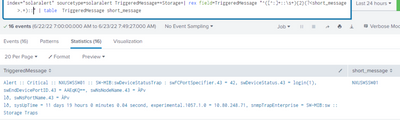
It's working fine for the events without spaces now and for events with spaces,there are some events(not all) which i highlighted earlier,not working.Below is the one
Alert :: Critical :: NXUSWSSW01 :: SW-MIB:swDeviceStatusTrap : swFCPortSpecifier.43 = 42, swDeviceStatus.43 = login(1), swEndDevicePortID.43 = AAEqKQ==, swNsNodeName.43 = ÀPv
lð, swNsPortName.43 = ÀPv
lð, sysUpTime = 11 days 19 hours 0 minutes 0.04 second, experimental.1057.1.0 = 10.80.248.71, snmpTrapEnterprise = SW-MIB:sw :: Storage Traps
Not sure what could be the issue.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
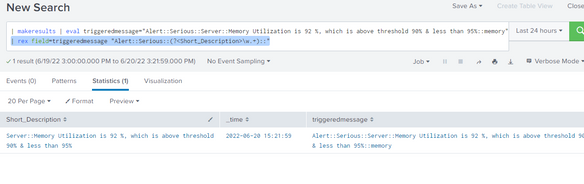
Use this:
| rex field=triggeredmessage "Alert::Serious::(?<Short_Description>\w.+)::"
Please Mark as Answer or Upvote if this is correct.