Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Splunk Search
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- Splunk Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- How could I edit my search command in order to fil...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jennifer
Path Finder
01-30-2022
06:34 AM
Hi, all!
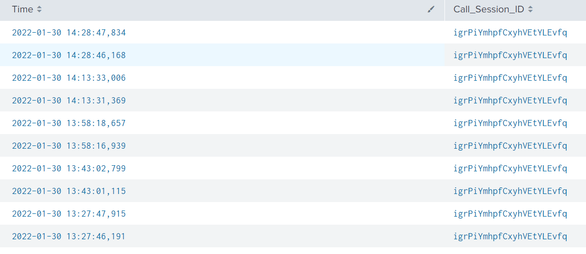
How could I edit my search command in order to filter this table which will display the earliest time of the same value(Call_Session_ID)?
Here is my original search command:
index="hkcivr" source="/appvol/wlp/DIVR01HK-AS01/applogs/progresshk.log*"| table Time Call_Session_ID
1 Solution
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
richgalloway

SplunkTrust
01-30-2022
07:09 AM
I'm not certain what you want as a final result, but perhaps this will help.
index="hkcivr" source="/appvol/wlp/DIVR01HK-AS01/applogs/progresshk.log*"
| stats min(_time) as Time by Call_Session_ID
| table Time Call_Session_ID
---
If this reply helps you, Karma would be appreciated.
If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
richgalloway

SplunkTrust
01-30-2022
07:09 AM
I'm not certain what you want as a final result, but perhaps this will help.
index="hkcivr" source="/appvol/wlp/DIVR01HK-AS01/applogs/progresshk.log*"
| stats min(_time) as Time by Call_Session_ID
| table Time Call_Session_ID
---
If this reply helps you, Karma would be appreciated.
If this reply helps you, Karma would be appreciated.
Get Updates on the Splunk Community!
Enterprise Security Content Update (ESCU) | New Releases
Last month, the Splunk Threat Research Team had two releases of new security content via the Enterprise ...
Detecting Remote Code Executions With the Splunk Threat Research Team
REGISTER NOWRemote code execution (RCE) vulnerabilities pose a significant risk to organizations. If ...
Observability | Use Synthetic Monitoring for Website Metadata Verification
If you are on Splunk Observability Cloud, you may already have Synthetic Monitoringin your observability ...