- Splunk Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Re: Spl
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Splunkers!!
Below is the search where we are comparing the last 3 hours vs 1 week ago data. How can we use dynamic token here? So when they select 2 hours it will compare 2 hours vs last 1 week ago.
How can we use token here in place of -3h : ((earliest=@m-3h latest=@m) OR (earliest=@m-1w-3h latest=@m-1w))
index=ecomm_sfcc_prod sourcetype=sfcc_logs source="/mnt/webdav/*.log" "Order created successfully" ((earliest=@m-3h latest=@m) OR (earliest=@m-1w-3h latest=@m-1w))
| eval time=date_hour.":".date_minute
| eval date=date_month.":".date_mday
| chart count by time date
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Why did you add brackets?
(earliest=@m$earliest_tok$ latest=@m) OR (earliest=@m-1w$earliest_tok$)or change the values in the option e.g.
<choice value="60m">Last 60 Minute</choice>and use:
(earliest=@m-$earliest_tok$ latest=@m) OR (earliest=@m-1w-$earliest_tok$)- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
index=ecomm_sfcc_prod sourcetype=sfcc_logs source="/mnt/webdav/*.log" "Order created successfully" ((earliest=@m-$hours$h latest=@m) OR (earliest=@m-1w-$hours$h latest=@m-1w))
| eval time=date_hour.":".date_minute
| eval date=date_month.":".date_mday
| chart count by time date- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have used the below approach in the dshboard but when I am passing the token "period_tok" in the panels like as suggested it is not working properly. I am getting the error like " Invalid value"@m-60m@m" . How can fix this issue.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You shouldn't have two @ symbols in the time - remove these from the token option values
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@ITWhisperer I have made the changes but it is still throwing me the same error.
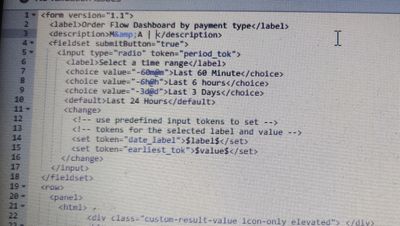
Below are the things I have attached for dashboard & the query. Please check at once
Dashboard :
<form version="1.1">
<label>Order Flow Dashboard by payment type</label>
<description>M&A |</description>
<fieldset submitButton="true">
<input type="radio" token="period_tok">
<label>Select a time range</label>
<choice value="-60m">Last 60 Minute</choice>
<choice value="-6h">Last 6 hours</choice>
<choice value="-3d">Last 3 Days</choice>
<default>Last 24 Hours</default>
<!-- set condition based on the label defined by <choice> -->
<!-- Within each condition, specify a custom label for display -->
<!-- Capture the selected value in the token, earliest_tok -->
<change>
<condition label="Last 24 Hours">
<set token="date_label">Yesterday</set>
<set token="earliest_tok">$value$</set>
</condition>
<condition label="Last 7 Days">
<set token="date_label">Last week</set>
<set token="earliest_tok">$value$</set>
</condition>
<condition label="Last 30 Days">
<set token="date_label">Last month</set>
<set token="earliest_tok">$value$</set>
</condition>
</change>
</input>
</fieldset>
Query used in the panels:
index=ecomm_sfcc_prod sourcetype=sfcc_logs source="/mnt/webdav/*.log" "Order created successfully" ((earliest=@m-$earliest_tok$ latest=@m) OR (earliest=@m-1w-$earliest_tok$ latest=@m-1w))
| eval time=date_hour.":".date_minute
| eval date=date_month.":".date_mday
| chart count by time date
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Your token value has a leading minus and you have a minus in the search so you will end up with two adjacent minus signs! Remove one of them.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@ITWhisperer Issue persist the same.
I think issue only with this search criteria.
I am using : (earliest=@m-($earliest_tok$) latest=@m) OR (earliest=@m-1w-($earliest_tok$)
I have tried this also but no luck :
(earliest=@m-("$form.earliest_tok$") latest=@m) OR (earliest=@m-1w-("$form.earliest_tok$")
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Why did you add brackets?
(earliest=@m$earliest_tok$ latest=@m) OR (earliest=@m-1w$earliest_tok$)or change the values in the option e.g.
<choice value="60m">Last 60 Minute</choice>and use:
(earliest=@m-$earliest_tok$ latest=@m) OR (earliest=@m-1w-$earliest_tok$)- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
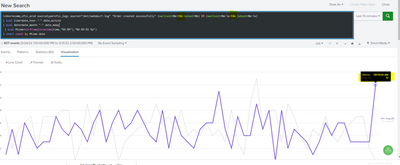
@ITWhisperer Thanks for fixing this. I am almost done with this approach , corrected the labels in the set tokens in the dashboard. Now after selecting the choices it is giving me the results. But I have only one concern. In the below screen when I am selecting the last 60 min comparison to last week. I have received some fishy timeframe results. In the graph you can see 9:19 am IST. It should be around 1:45 PM IST rater than this.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@ITWhisperer Thanks for your response let me check with this approach. However you are constructor of this query.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@tread_splunk Looking perfect and while I am selecting it is showing the same date and same timeframe comparison.
But here when I am slecting the any timeframe the time is looking like in yellow highlighted. How can I chnage it in human readable format.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @uagraw01 What human readable format do you want?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@tread_splunk Actually when I am selecting any time frame I am not getting the exact timeframe of data.
Ex : If I have select 2 hours :- then should compare last 2 hours vs last week
If I am using the below query :
index=ecomm_sfcc_prod sourcetype=sfcc_logs source="/mnt/webdav/*.log"
[| makeresults
| addinfo
| eval last_week_min=info_min_time-(60*60*24*7), last_week_max=info_max_time-(60*60*24*7)
| eval search="(earliest>".last_week_min." latest<".last_week_max.") OR (earliest>".info_min_time." latest<".info_max_time.")"]
| eval time=date_hour.":".date_minute
| eval date=date_month.":".date_mday
| chart count by time date
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Not sure you can tokens for that. Will wait and see what response you get. The following looks like it works for me...
index=blah AND
[| makeresults
| addinfo
| eval last_week_min=info_min_time-(60*60*24*7), last_week_max=info_max_time-(60*60*24*7)
| eval search="(earliest>".last_week_min." latest<".last_week_max.") OR (earliest>".info_min_time." latest<".info_max_time.")"]Choose the time range you want from the time picker (last 5 mins, last 3hrs, or a time range) and then the subquery returns the earliest / latest combination for that period AND the same period a week ago (i.e. 60*60*24*7 secs ago).
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@tread_splunk Thanks for your response. In your query how can we compare two time frame dynamically.
Like : 3 hours ago vs 1 week ago
24 hours vs 48 hours ago
6 hours vs 1 week ago.
Means when user select any time frame than both will chnage
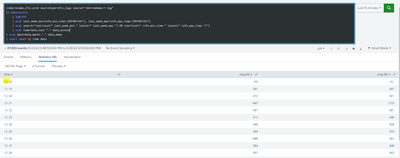
Please see below screenshot: