- Splunk Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Help to assign values in increment order to each v...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
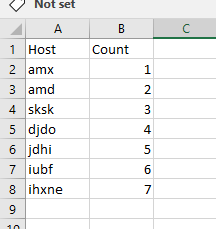
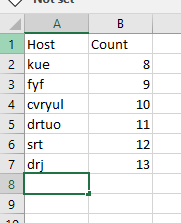
Help to assign values in increment order to each values in a field
It should assign values to each values in the specific field,
if the same query executes at second time, it should start with previously ended values, i.e.., from 8
This should be continue at every time the query executes.
consider this is the search,
index=linux host="*" memUsedPct="*" sourcetype="vmstat" earliest=-60m latest=-1m
| eval host=mvindex(split(host,"."),0)
| stats avg(memUsedPct) AS memUsedPct by host
| eval memUsedPct=round(memUsedPct,1)
| where (memUsedPct>80 AND memUsedPct<90)
,This will return list of host, it should be numbered from 1, and if the next time query runs, it should start from previous value,
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Ok, a very ugly solution would be to capture results in a lookup and in the subsequent run have a subsearch which would select max(count). Then you'd eval one field to it and streamstats count and add this constant field.
But I won't write the search itself here because it's a very ugly solution, it's not "splunky" in my opinion and it will probably have huge problems with race condition.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
One question to consider with such requests - if you have several million rows to return and your search started at 12:31:12 and lasted till 12:31:42. And another person started "the same" search at 12:31:31. How should his results be numbered and why?
Anyway, Splunk does not - without some magic - have the concept of "state" stored between different searches.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It wont return more than 10 values,
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
There doesn't appear to be anything in your search that would specifically limit the number of events returned - why do you think there are no more than 10?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You're dodging the question, not answering it. OK, what if there were two instances run at the same time?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
For testing stuff i sometimes do the following search for incremental counts:
| makeresults count=10 ```for generating 10 tablerows```
| streamstats count ```for count upwards with the rows, starting with 1```
For "saving" the last count you could write that into an Index or into a Lookup or count the data that already got counted incrementally. and add that to a new incremental count.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It is not clear where these queries are executing - normally, if you execute a search against a dataset, you will get results from that dataset. Unless that dataset is updated in some way, your results won't change. Having said that, within a dashboard, you might be able to save the highest value from one execution of a search in a token (for example) and use the value of the token to add to the counts the next time the search executes.