- Splunk Answers
- :
- Splunk Administration
- :
- Security
- :
- data segregation methods
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
data segregation methods
hello -
i've been reading the various guides and some other Q&As regarding segration or role-based access to different data.
i'm working with a distributed environment, where there are separate forwarders in each "region" which feeds into centralised indexer / search tiers. data needs to be segregated based on its home "region", or where the data originates from in other words.
so i'll somehow need to identify the data based on where it came from originally, either based on originating host, forwarder, or something like that.
right now - i've got a demo that i think appears to be working, where i force data sourced in a particular region into different indexes, based on inputs.conf. i then use RBAC (with AD group mappings) to control access based on index. i also need to modify the dashboards / saved searches within our app because this impacts summarization of the indexed data. i can also perhaps imagine a use for "tags" or something similar as the default search terms...
any ideas? any recommendations and/or words of wisdom?
the use case is Cisco IronPort WSA access logs... feeding into a Splunk for WSA app deployment.
cheers,
andrew
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
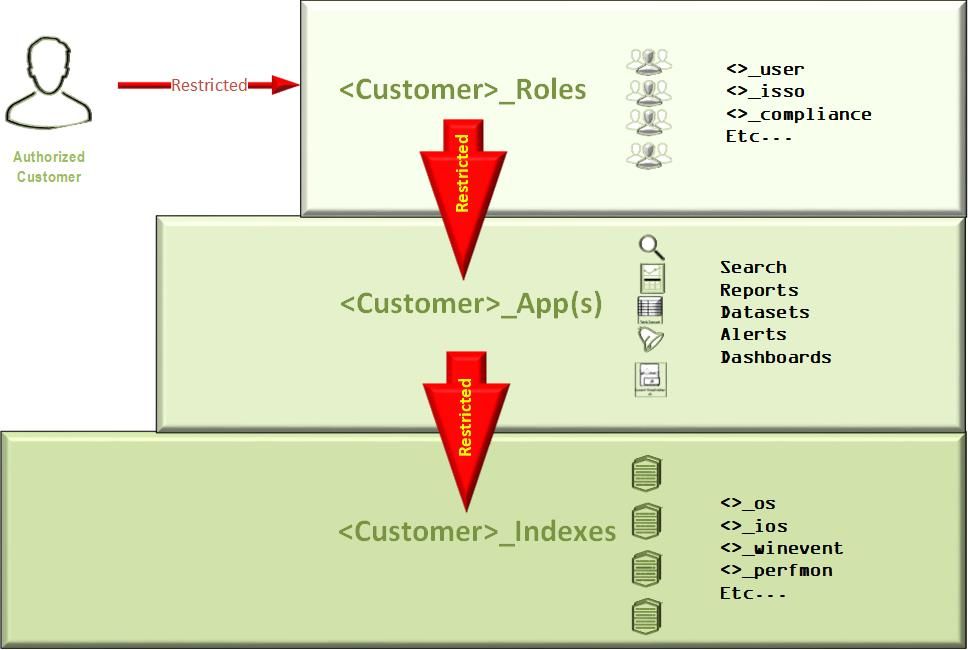
Our solution is to create indexes for each customer whose data needs to be segregated from the rest. Customer apps are slaved to indexes and customer roles are slaved to their respective apps. The apps can be locked down so that they only see the indexes that are needed and mitigates any one customer traversing the data of other customers or us for that matter.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
if you tag your data via the forwarders which I assume are in your various regions, then this tag could then be used to segment your data into the different indexes and then use RBAC via the AD groups to finely control access to the data.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Having separate indexes for each region will help you restrict user-access to their respective indexes only.
Haven't implemented it so far, however, these roles/restrictions should work even at App level too.
Will be interesting to know the solution.
Br, Mitesh.