- Splunk Answers
- :
- Using Splunk
- :
- Other Usage
- :
- Re: How to avoid duplicate alerts for 1 month of t...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How to avoid duplicate alerts for 1 month of timespan
Hi,
I have a alert scheduled to monitor, if 2 different users who are accessing same device for authentication from okta and I'm monitoring it for 1 month.
Once the alert is triggered , the same users details should not trigger for next 1 month. Any suggestions how can I achieve this ? ( Can be in query / alert actions )
Below is sample query:
index=okta result=success NOT ( device=null)
| eval _time=strftime(_time)
| stats values (user ) as user dc(user) as "number of users per device" by device _time
| lookup XXX
| search "number of users per device">1
| regex device =myregx| rex field=user (myregex)
| where isnull(match)
| table fileds
| stats fields X y Z dc(_time) as detected by device
| where detected>=1
| sort _time
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I mean by adding threshold conditions ?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@richgalloway and @ITWhisperer / Team ,
Apart from Throttling is there any way which we can automate the query / alert ? I'm looking to automate from query more over manual alert settings . Any suggestions will be helpful. Thank You.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Alerts are automated. That is their nature. Configurations can be manual, but are a one-time action.
Remember that each time an alert runs it is independent of other runs (context-free). If you need context, other than what is provided by the throttling option, then you'll have to implement it yourself.
Triggering users/devices can be saved in a lookup file, KVStore, or (as @ITWhisperer suggested), a summary index. The alert would need to consult the saved list to see if a new alert should be triggered or not.
If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What is it you are trying to automate? There is no generic way of doing this, you need to find a way which suits your situation.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Throttling alerts will stop the alert from being triggered, however, it is at the alert level, that is, if the alert should be triggered for a different user, I doubt if this would fire if you had a throttle on the alert.
What you could do is collect the results of the alert in a summary index and check against the summary index if the alert has been triggered for the user(s) within the last month.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
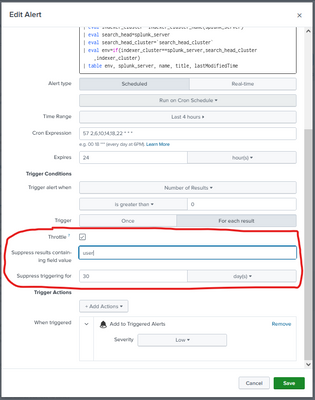
Throttling of alerts is not done using SPL. To enable throttling, edit the alert and check the "Throttle" box. Enter the time between alerts and click Save.
If this reply helps you, Karma would be appreciated.