- Splunk Answers
- :
- Splunk Administration
- :
- Monitoring Splunk
- :
- Re: Error "Duplicate Servername"
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Error "Duplicate Servername"
Hi
We are getting the following error message while accessing any application.
Unable to distribute to peer named
Regards
Rajesh
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
did u try disable distribution search ?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
enable and disable done.
But there is no difference.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
A non-Splunk specific cause might be a fat-fingered entry in the systems hosts file, or in the DNS entry for the server name listed in the "at uri" portion of the error message.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
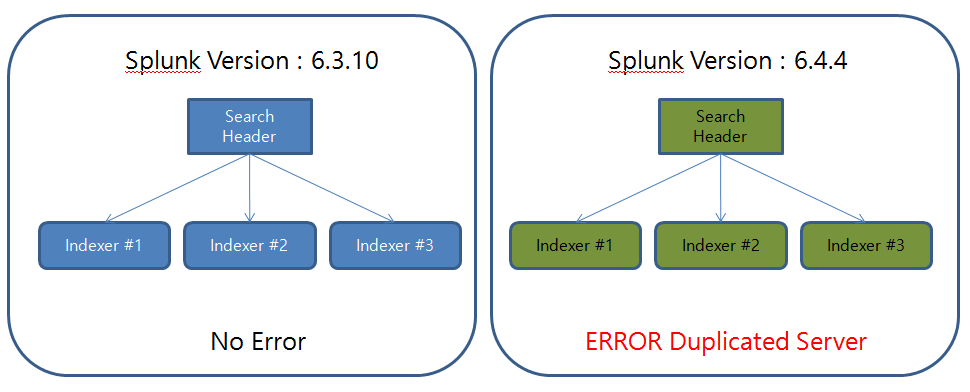
I used vmware.
I have installed one server 6.3.10 and 6.4.4.
The configuration is one search header and three indexers.
I finished the configuration and restarted the search header.
Then I searched the search-header below.
- search query : index=_internal source=*splunkd.log log_level=ERROR Distribute
The results below only appear in 6.4.4.

6.3.10 search header distribute search detail

- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Ok, let me get it clearly.! You have total 3 indexer and 2 search heads. Both are in different version. Do you have any counter master?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Correction. Cluster master
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
So its like 1 search head + 3 indexer at 6.3 and a search head + 3 indexer at 6.4.
Total 8 server, 2 different groups. Right?
Please pasted splunk.Log here from server.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
From your previous post figures where you put search head 6.4 that was showing error. I observed indexer are same in both search head. 192.168.88.130 and 192.168.88.131.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What's current config is like. Please paste all detail like SH names and which connectior is linked with which search head
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
When I paste the contents of Splunkd.log, the following message is displayed.
"Your comment was submitted, and will be reviewed by a moderator before being visible to all users."
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What's current config is like. Please paste all detail like SH names and which connectior is linked with which search head
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-01-2017 23:48:18.159 +0900 INFO ClusteringMgr - clustering disabled
05-01-2017 23:48:18.159 +0900 INFO SHClusterMgr - initing shpooling with: ht=60 rf=3 ct=60 st=60 rt=60 rct=5 rst=5 rrt=10 rmst=600 rmrt=600 pe=1 im=0 is=0 mor=5 pb=5 rep_port= pptr=10
05-01-2017 23:48:18.159 +0900 INFO SHClusterMgr - shpooling disabled
05-01-2017 23:48:18.159 +0900 INFO PipelineComponent - registering timer callback name=DistributedRestCallerCallback callback=0x7f2709a51590 arg=0x7f2706365080 size=4 aborts=0x0 gen=4 accCbMsecs=0ms
05-01-2017 23:48:18.264 +0900 ERROR DistributedPeer - Peer:https://192.168.88.130:8090 Duplicate Servername
05-01-2017 23:48:18.264 +0900 ERROR DistributedPeer - Peer:https://192.168.88.131:8090 Duplicate Servername
05-01-2017 23:48:18.264 +0900 INFO ServerRoles - Declared role=search_head.
05-01-2017 23:48:18.264 +0900 INFO IndexerInit - running splunkd specific init
05-01-2017 23:48:18.271 +0900 INFO IndexerService - indexes.conf - indexThreads param autotuned to=2
05-01-2017 23:48:18.271 +0900 INFO IndexerService - indexes.conf - memPoolMB param autotuned to=64MB
05-01-2017 23:48:18.271 +0900 INFO MPool - MPool initialized: bytes=67108864
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I changed the general stanzas of the three indexers.
Indexer #1 server.conf
[general]
serverName = server_22
pass4SymmKey = $1$tvTHmsS5kq97
Indexer #2 server.conf
[general]
serverName = server_33
pass4SymmKey = $1$oQ/VgulsS5WG
Indexer #3 server.conf
[general]
serverName = server_44
pass4SymmKey = $1$ZjxhnZAKdFJe
My Search Header splunkd.log
05-02-2017 10:05:24.103 +0900 ERROR DistributedPeer - Peer:https://192.168.88.130:8090 Duplicate Servername
05-02-2017 10:05:24.085 +0900 ERROR DistributedPeer - Peer:https://192.168.88.131:8090 Duplicate Servername
05-02-2017 10:05:24.085 +0900 ERROR DistributedPeer - Peer:https://192.168.88.130:8090 Duplicate Servername
Indexers do not show error logs.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-01-2017 23:48:18.264 +0900 ERROR DistributedPeer - Peer:https://192.168.88.130:8090 Duplicate Servername
05-01-2017 23:48:18.264 +0900 ERROR DistributedPeer - Peer:https://192.168.88.131:8090 Duplicate Servername
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What's current config is like. Please paste all detail like SH names and which indexer is linked with which search head
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The log is not strangely attached.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I tried several times, but I can not paste all the logs from splunkd.log.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I compared version 6.3.10 and version 6.4.4.
I installed Splunk and set up distributed search only.
There was no such error in 6.3.10.
"ERROR DistributedPeer - Peer: https: //192.168.88.131: 8090 Duplicate Servername"
However, since using version 6.4.4, this error message has occurred.
Why do I get this message?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi khyoung7410,
what is the current set up of your splunk? where you seeing this error and is it for an indexer?
check the setting> distributed search> search peer detail and server.conf