- Splunk Answers
- :
- Splunk Administration
- :
- Getting Data In
- :
- Re: Sysmon events not getting indexed
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
I am deploying sysmon all acrros our company but for some reason the sysmon events are not getting indexed
Our deployment is the following:
- Splunk 9.0.5 running on Windows server
- sysmon index created manually in Splunk.
- inbound firewall rules created allowing traffic TCP in port 9997
- Sysmon TA installed in the server in C:\Program Files\Splunk\etc\deployment-apps\Splunk_TA_microsoft_sysmon
- default/input.cont enabled (by default)
[WinEventLog://Microsoft-Windows-Sysmon/Operational]
disabled = false
renderXml = 1
source = XmlWinEventLog:Microsoft-Windows-Sysmon/Operational
- local/input.conf containing
[WinEventLog://Microsoft-Windows-Sysmon/Operational]
index=sysmon
- Splunk Universal forwarder 9.1.0 deployed in all hosts
- All UF are reporting correctly to Splunk
- confirmed that sysmon TA is present in all hosts , deployed via forwarder management using a server class
- /etc/system/default/ouputs.conf is pointing to the right splunk server
[tcpout]
defaultGroup = default-autolb-group
[tcpout:default-autolb-group]
server = xxxxxx:9997
[tcpout-server://xxxxxx:9997]
- Sysmon 15 deployed in all hosts
- confirmed that the events are being created locally in the hosts in Microsoft-->Windows-->Sysmon tree
But no single event appears in the sysmon index 😞
Does anyone have any idea or suggestion of what might be missing?
many thanks
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I finally found the reason. it was due to the user configured to run the Splunk forwarder windows service. It was a local user account without necessary rights. I changed it to local system account and the events started to flow in.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
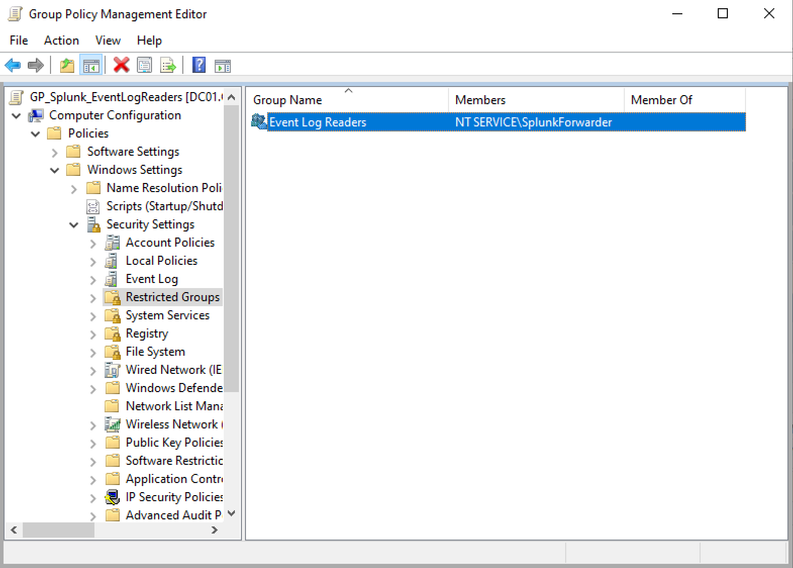
If you want to run SplunkForwarder with virtual account (which is recommended if you want to follow princpile of the least privileges) there is also a way to enable reading of sysmon logs. NT SERVICE/SplunkFowarder needs to be added to Event Log Readers group.
One of the ways is to add it to the Group policy and deploy it accross your environment where your Forwarders are installed.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have the same issue, how do you all solve it guys?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
in my case the issue was the user running the splunk universal forwarder service.
open the services manager and check that, it should be SYSTEM or any user with local admin rights
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I finally found the reason. it was due to the user configured to run the Splunk forwarder windows service. It was a local user account without necessary rights. I changed it to local system account and the events started to flow in.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
hi @corti77
I'm getting the same error, but my Splunk UF is running as Administrator
But I still get the same error. I wonder if there is any other way to fix this error ?
Thanks
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
try to configure it with the user SYSTEM. if the issue persists, check the local logs of the universal forwarder located in c:\program files\splunk\var\log\splunkd.log
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I found the reason but not the solution. at the host level , the splunk forwarder does not have access to the sysmon event logs for some unknown reason.
any idea?
08-25-2023 16:34:02.254 +0200 ERROR ExecProcessor [1340 ExecProcessor] - message from ""C:\Program Files\SplunkUniversalForwarder\bin\splunk-winevtlog.exe"" splunk-winevtlog - WinEventLogChannel::subscribeToEvtChannel: Could not subscribe to Windows Event Log channel 'Microsoft-Windows-Sysmon/Operational'
08-25-2023 16:34:02.254 +0200 ERROR ExecProcessor [1340 ExecProcessor] - message from ""C:\Program Files\SplunkUniversalForwarder\bin\splunk-winevtlog.exe"" splunk-winevtlog - WinEventLogChannel::init: Init failed, unable to subscribe to Windows Event Log channel 'Microsoft-Windows-Sysmon/Operational': errorCode=5- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Do you find any solution for this?
I have some UFs that run with local system and they can send sysmon logs but I have some UFs that run with virtual account and therefore they can't send sysmon logs.
I have the same message as you.