- Splunk Answers
- :
- Using Splunk
- :
- Alerting
- :
- how to configure splunk to send all alerts in one ...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
how to configure splunk to send all alerts in one email ?
Hello all,
It's my second day with a Splunk and I cant understand a splunk logic. I created a alert search. It works fine. As a search result I have a table:
IP address username broken_rule count_of_broken_rules
192.168. ... aaa rule_name 75
192.168... bbb rule_name 74
199.188... ccc rule_name 20
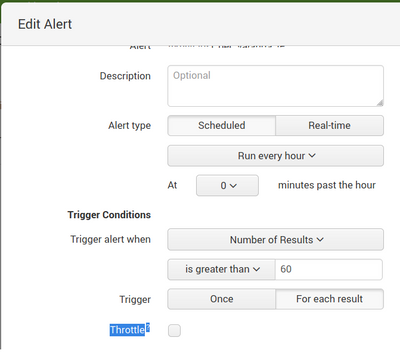
How can You see in picture, I configured alert to send an email when count of broken rules is more than 60. It must to send an email every hour. If I choose an option "Once" I am getting an email only with a one (first) record. But I want to get an email with a second record too. If i choose an option "for each result" I am getting an email for all records. It doesnt matter, that the the third record does not meet the requirement> 60. I want to get one email with the two record (from a example with first and second records). What I am doing wrong?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@richgalloway
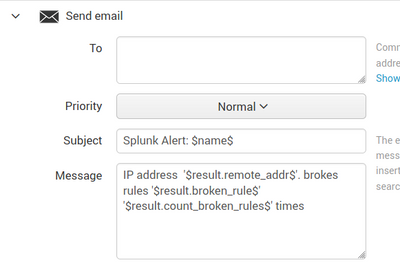
Thanks for an answer. I will try it. But how to configure Splunk, that it will send an email with all records in one email?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You did that before. Select the "Trigger Once" option. That's always worked for me and I've never had an alert contain only the first result.
If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @richgalloway
Does your email "message" field has any text? I wrote in this field this text. Maybe it is a reason, why I am getting email only with the first result?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, I always include something in the Message field.
If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The alert is set to trigger when the number of results is greater than 60, without regard to the value of the results.
In my experience, it's better to have the alert search for and show only the results that meet the criteria for the alert. For instance
... | where count_of_broken_rules > 60then set the alert to trigger when the number of results is not zero.
If this reply helps you, Karma would be appreciated.