- Splunk Answers
- :
- Splunk Administration
- :
- Installation
- :
- How to get Splunk license utilization for the las...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How to get Splunk license utilization for the last 3 months
Can you please let us know how to get Splunk license utilization for the last 3 months.
We would like to know through query.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @pratapa,
you can use the usual dashboard with license usage and modify it for a period of 90 days instead 30 days:
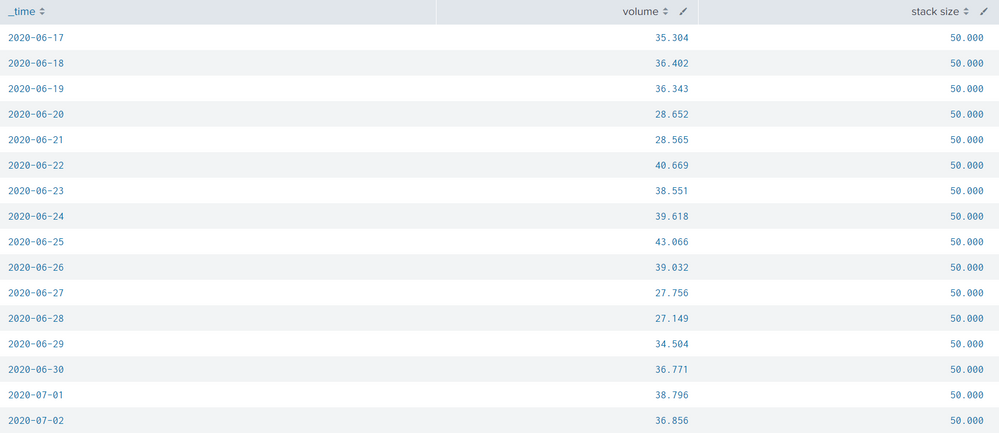
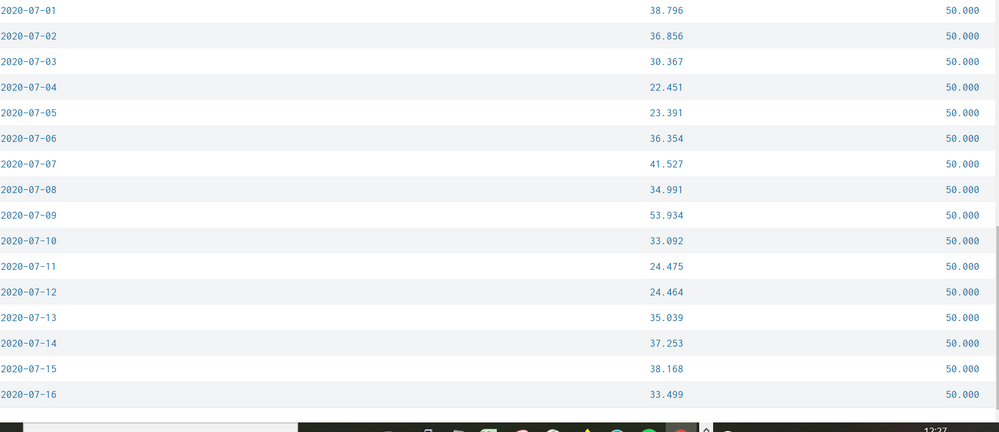
index=_internal [`set_local_host`] source=*license_usage.log* type="RolloverSummary" earliest=-90d@d
| eval _time=_time - 43200
| bin _time span=1d
| stats latest(b) AS b by slave, pool, _time
| timechart span=1d sum(b) AS "volume" fixedrange=false
| join type=outer _time [search index=_internal [`set_local_host`] source=*license_usage.log* type="RolloverSummary" earliest=-90d@d
| eval _time=_time - 43200
| bin _time span=1d
| dedup _time stack
| stats sum(stacksz) AS "stack size" by _time]
| fields - _timediff
| foreach * [eval <<FIELD>>=round('<<FIELD>>'/1024/1024/1024, 3)]
or to use the Splunk License Usage App ( https://splunkbase.splunk.com/app/174/ ).
Only one attention: be sure that the retention of _internal index is more than 90 days, otherwise you haven't your results.
Ciao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @gcusello ,
I ran the following query but able to get only last 30 days license uasge.
Could you please suggest what modifications needs to be done to get last 90 days usage.
index=_internal source=*license_usage.log* type="RolloverSummary" earliest=-90d@d
| eval _time=_time - 43200
| bin _time span=1d
| stats latest(b) AS b by slave, pool, _time
| timechart span=1d sum(b) AS "volume" fixedrange=false
| join type=outer _time [search index=_internal source=*license_usage.log* type="RolloverSummary" earliest=-90d@d
| eval _time=_time - 43200
| bin _time span=1d
| dedup _time stack
| stats sum(stacksz) AS "stack size" by _time]
| fields - _timediff
| foreach * [eval <<FIELD>>=round('<<FIELD>>'/1024/1024/1024, 3)]
Regards,
Rahul
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @rahul2gupta,
probably the problem isn't on the search but on the logs: internal logs has usually a retention of 30 days.
if you want more than 30 days, you have to extend the retention period of _internal index (with more storage occupation, or schedule a search that every night calculate the sum of day license consumption and store this information in a summary index.
Ciao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi at all,
thank you for your Karma Point, please, accept the answer for the other people of the Community.
Ciao and next time.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
it needs that your retention time for _internal is at least 90 days.