Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Getting Data In
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- Splunk Answers
- :
- Splunk Administration
- :
- Getting Data In
- :
- How to extract only the values that has the same t...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
danielgp89
Path Finder
01-18-2019
10:07 AM
Hello!
I have events from two different fields that are correlate each other by the time.
So I want to make a table extracting only those values that were generate at the same time from a range of time of one day.
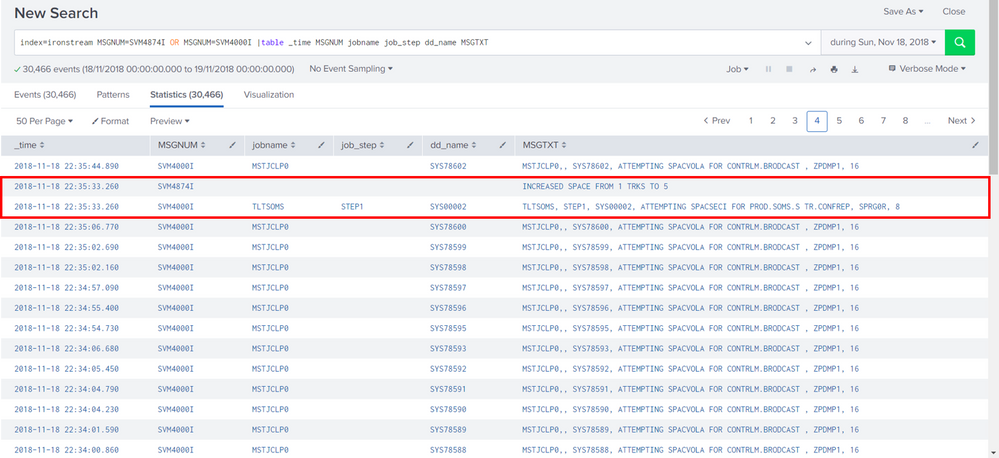
For example in the table below, there are two values that has the same time:
How can I extract the events that only has the same timestamp from those two fields (MSGNUM=SVM4000I and SVM4874I)
1 Solution
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
renjith_nair

SplunkTrust
01-18-2019
08:43 PM
@danielgp89,
Try this and verify if its working for you
"your base search"|eventstats dc(MSGNUM) as c by _time|where c>1
This should result only those events which has at least 2 MSGNUM values of same time
Happy Splunking!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
renjith_nair

SplunkTrust
01-18-2019
08:43 PM
@danielgp89,
Try this and verify if its working for you
"your base search"|eventstats dc(MSGNUM) as c by _time|where c>1
This should result only those events which has at least 2 MSGNUM values of same time
Happy Splunking!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
danielgp89
Path Finder
01-20-2019
06:04 PM
Thanks so much Renjith!
Your going to heaven!
Get Updates on the Splunk Community!
Routing logs with Splunk OTel Collector for Kubernetes
The Splunk Distribution of the OpenTelemetry (OTel) Collector is a product that provides a way to ingest ...
Welcome to the Splunk Community!
(view in My Videos)
We're so glad you're here!
The Splunk Community is place to connect, learn, give back, and ...
Tech Talk | Elevating Digital Service Excellence: The Synergy of Splunk RUM & APM
Elevating Digital Service Excellence: The Synergy of Real User Monitoring and Application Performance ...