Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Splunk Search
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- Splunk Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- How do I do maths with the results of a search for...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How do I do maths with the results of a search for the results that I'm actually after
ruiner314
New Member
11-28-2018
02:46 PM
I have a search similar to this that gets me stats that are the first step in what I'm after:
index=balloons
| stats count by COLOR
COLOR Count
Grey 6
Purple 5
Orange 27
Red 8
Blue 1
Yellow 9
But I want to know now is what percentage of those that aren't grey are blue or purple. Something to the effect of this:
(Count(Blue) + Count(Purple))/(Count(Purple)+Count(Orange)+Count(Red)+Count(Blue)+Count(Yellow))
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
woodcock
Esteemed Legend
11-28-2018
08:38 PM
Better yet, like this:
index=balloons
| eval foo="bar"
| chart count OVER foo BY COLOR
| addtotals row=t col=f
| eval ANSWER = (Blue + Purple) / Total
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
woodcock
Esteemed Legend
11-28-2018
08:12 PM
Like this:
| makeresults | eval raw="Grey 6:::Purple 5:::Orange 27:::Red 8:::Blue 1:::Yellow 9"
| fields - _time
| makemv delim=":::" raw
| mvexpand raw
| rename raw AS _raw
| rex "^(?<COLOR>\S+)\s+(?<count>\d+)$"
| fields - _raw
| rename COMMENT AS "Everything above generates sample summary data; everything below is your solution; you would start with 'index=baloons | stats count BY COLOR'"
| eval foo="bar"
| xyseries foo COLOR count
| addtotals row=t col=f
| eval ANSWER = (Blue + Purple) / Total
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
HiroshiSatoh
Champion
11-28-2018
08:01 PM
Try this!
index=balloons| stats count by COLOR
| transpose header_field=COLOR 100
| fields - column
| eval your_field=(Blue+Purple)/(Purple+Orange+Red+Blue+Yellow)
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
adonio
Ultra Champion
11-28-2018
07:50 PM
hello there,
not the prettiest solution, but it works.
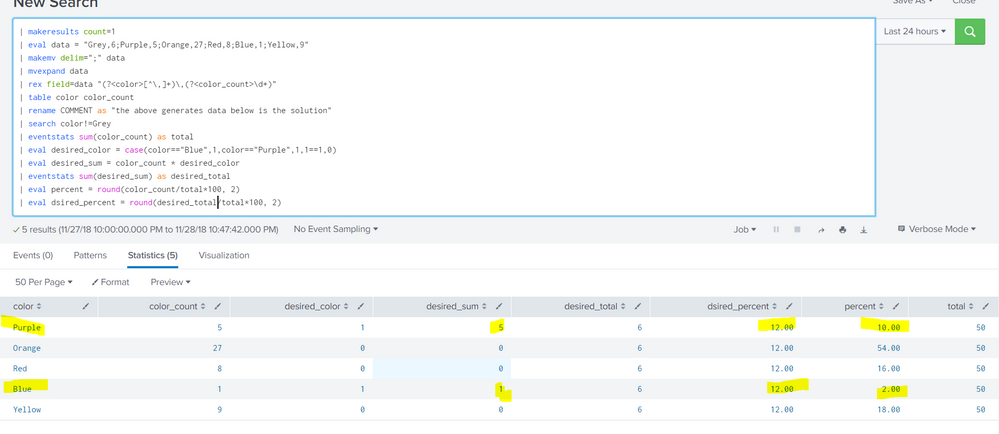
try the following search anywhere and see screenshot:
| makeresults count=1
| eval data = "Grey,6;Purple,5;Orange,27;Red,8;Blue,1;Yellow,9"
| makemv delim=";" data
| mvexpand data
| rex field=data "(?<color>[^\,]+)\,(?<color_count>\d+)"
| table color color_count
| rename COMMENT as "the above generates data below is the solution"
| search color!=Grey
| eventstats sum(color_count) as total
| eval desired_color = case(color=="Blue",1,color=="Purple",1,1==1,0)
| eval desired_sum = color_count * desired_color
| eventstats sum(desired_sum) as desired_total
| eval percent = round(color_count/total*100, 2)
| eval dsired_percent = round(desired_total/total*100, 2)
screenshot:
hope it helps
Get Updates on the Splunk Community!
Routing logs with Splunk OTel Collector for Kubernetes
The Splunk Distribution of the OpenTelemetry (OTel) Collector is a product that provides a way to ingest ...
Welcome to the Splunk Community!
(view in My Videos)
We're so glad you're here!
The Splunk Community is place to connect, learn, give back, and ...
Tech Talk | Elevating Digital Service Excellence: The Synergy of Splunk RUM & APM
Elevating Digital Service Excellence: The Synergy of Real User Monitoring and Application Performance ...