- Apps and Add-ons
- :
- All Apps and Add-ons
- :
- Splunk App for Windows - Missing Task Category, Ev...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
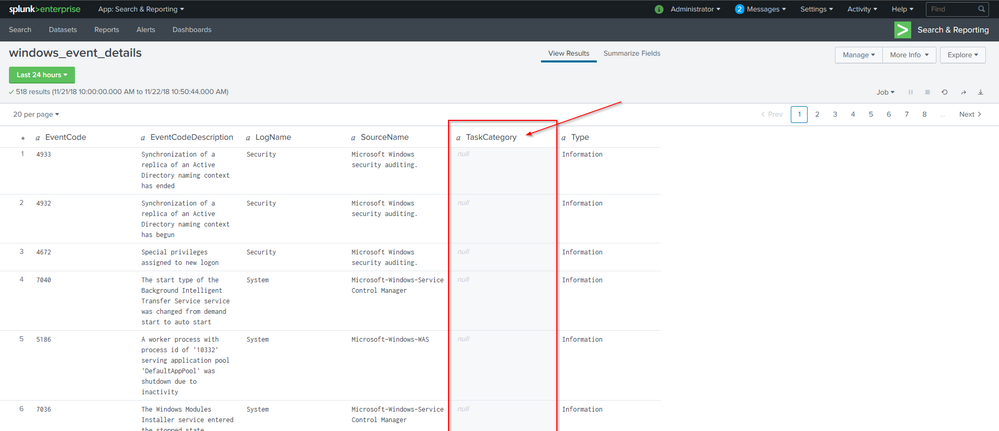
i've tried to implement the Splunk App for Windows and getting Events into the System. But i have a problem espacially with the Windows Event Monitoring Dashboard. There should be the fields Task Category, Event Code and Type populated but they are empty. So the Dashboard is not showing Data.
I've already looked at the lookup table that should populate this fields but the Task Category Field is empty.
I've followed the guide for implementing the app, so i think i've done everything corrept, but i'm totaly new to Splunk so i've maybe missed something.
Does anyone know how the Task Category Field is populated or can give me a hint what i'm missed?
Thanks in Advance
Stefan
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
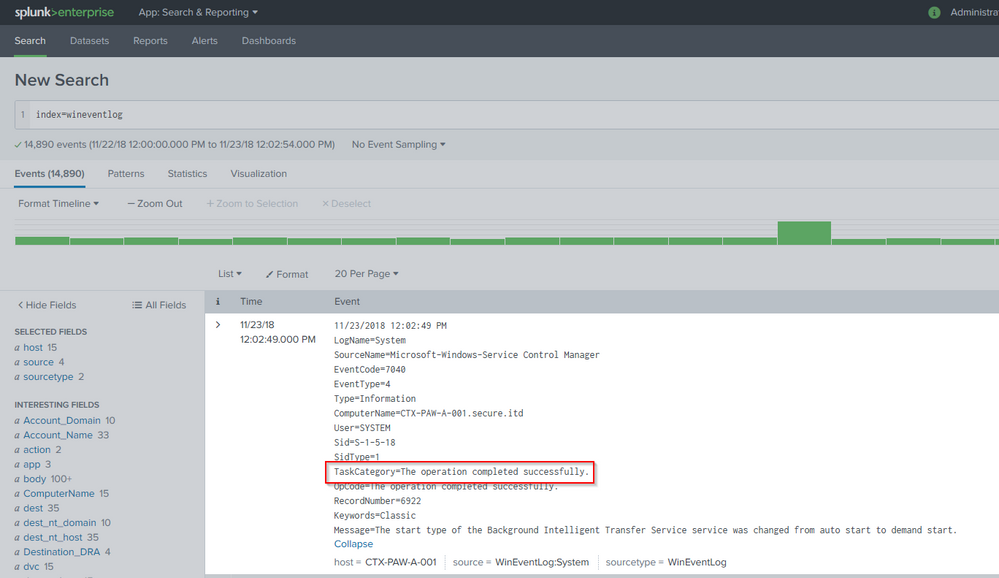
I finally identified the root cause of the Problem. It seems to me that there is a bug in the Default/props.conf of the splunk_app_windows_infrastructure. As soon as this app is deployed the TaskCategory Field is missing.
In the props.conf File is a Field alias defined which will Override the TaskCategory Field with empty Information from the CategoryString Field which does not exist, so both fields arent displayed in search.
###### Add an Alias for TaskCategory and CategoryString from the Windows Events #####
FIELDALIAS-CategoryString_for_windows = CategoryString as TaskCategory
I think the correct Configuration should be:
FIELDALIAS-CategoryString_for_windows = TaskCategory AS CategoryString
I think the fields CategoryString and TaskCategory got twisted. As soon as I correct the field order, I got TaskCategory and CategoryString as available Fields in Search.
Maybe someone can report this directly to the Splunk support Team, so they can fix it. I'm currently just evaluating the product so I have no support Agreement with them and cannot report Bugs. 🙂
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I finally identified the root cause of the Problem. It seems to me that there is a bug in the Default/props.conf of the splunk_app_windows_infrastructure. As soon as this app is deployed the TaskCategory Field is missing.
In the props.conf File is a Field alias defined which will Override the TaskCategory Field with empty Information from the CategoryString Field which does not exist, so both fields arent displayed in search.
###### Add an Alias for TaskCategory and CategoryString from the Windows Events #####
FIELDALIAS-CategoryString_for_windows = CategoryString as TaskCategory
I think the correct Configuration should be:
FIELDALIAS-CategoryString_for_windows = TaskCategory AS CategoryString
I think the fields CategoryString and TaskCategory got twisted. As soon as I correct the field order, I got TaskCategory and CategoryString as available Fields in Search.
Maybe someone can report this directly to the Splunk support Team, so they can fix it. I'm currently just evaluating the product so I have no support Agreement with them and cannot report Bugs. 🙂
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I can confirm - this is the definitely the issue!! Thanks hayduk - I will escalate this as much as I can
-ali from Splunk PS
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I apologize if my comment gets duplicated. I don't see my first attempted response though.
I had the same issue after updating this app to v5.0.1. I applied the suggested fix above and by all indications, it appears to have resolved the issue for me as well.
I've opened a case with Splunk to confirm this issue/resolution and request they fix it in a future revision.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Splunk responded to my case. They are aware of this issue and it is slated to be fixed in a future release of the app. They also confirmed the work around above is valid in the mean time.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Cool! Thats great!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Did you add winfra-admin role to your user?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes my user is has the winfra-admin role assigned. I think the Problem is more related to the Splunk Add-on for Microsoft Windows than to the Splunk 5.x App for Microsoft Windows. From my Point of view is the field extraction from the Windows Add-on not working properly.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Can you share your Universal Forwarder local\inputs.conf.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sure …
[WinEventLog://Application]
disabled = true
start_from = oldest
current_only = 0
checkpointInterval = 5
renderXml=false
index=wineventlog
[WinEventLog://Security]
disabled = 0
start_from = oldest
current_only = 0
evt_resolve_ad_obj = 1
checkpointInterval = 5
blacklist1 = EventCode="4662" Message="Object Type:(?!\s*groupPolicyContainer)"
blacklist2 = EventCode="566" Message="Object Type:(?!\s*groupPolicyContainer)"
blacklist3 = EventCode="5136" Message="Class:(?!\s*groupPolicyContainer)"
blacklist4 = 4689,4703,4985,4799,5158
blacklist5 = EventCode="4688" Message="(?:Process Name:).+(?:SplunkUniversalForwarder\\bin\\splunk.exe)|.+(?:SplunkUniversalForwarder\\bin\\splunkd.exe)|.+(?:Splunk UniversalForwarder\\bin\\btool.exe)"
blacklist6 = EventCode="4688" Message="(?:Process Name:).+(?:SplunkUniversalForwarder\\bin\\splunkwinprintmon.exe)|.+(?:SplunkUniversalForwarder\\bin\\splunkpowershell.exe)|.+(?:SplunkUniversalForwarder\\bin\\splunkregmon.exe)|.+(?:SplunkUniversalForwarder\\bin\\splunk-netmon.exe)|.+(?:SplunkUniversalForwarder\\bin\\splunkadmon.exe)|.+(?:SplunkUniversalForwarder\\bin\\splunkMonitorNoHandle.exe)|.+(?:SplunkUniversalForwarder\\bin\\splunkwinevtlog.exe)|.+(?:SplunkUniversalForwarder\\bin\\splunkperfmon.exe)|.+(?:SplunkUniversalForwarder\\bin\\splunk-wmi.exe)"
blacklist7 = EventCode="4688" Message="(?:Process Command Line:).+(?:--scheme)|.+(?:--no-log)|.+(?:-Embedding)"
blacklist8 = EventCode="4634" Message="(?:Account Name:).+(?:\$$)|.+(?:SYSTEM)"
blacklist9 = EventCode="4624" Message="(?:Account Name:).+(?:\$$)|.+(?:SYSTEM)"
renderXml=false
index=wineventlog
[WinEventLog://System]
disabled = 0
start_from = oldest
current_only = 0
evt_resolve_ad_obj = 1
checkpointInterval = 5
blacklist1 = SourceName="Microsoft-Windows-DistributedCOM"
blacklist2 = SourceName="Microsoft-Windows-Security-SPP"
blacklist3 = SourceName="Microsoft-Windows-LSA"
blacklist4 = SourceName="MsiInstaller"
renderXml=false
index=wineventlog
[WinEventLog://Microsoft-Windows-AppLocker/Packaged app-Execution]
checkpointInterval = 5
current_only = 0
disabled = 0
start_from = oldest
evt_resolve_ad_obj = 1
index=wineventlog
[WinEventLog://Microsoft-Windows-AppLocker/Packaged app-Deployment]
checkpointInterval = 5
current_only = 0
disabled = 0
start_from = oldest
evt_resolve_ad_obj = 1
index=wineventlog
[WinEventLog://Microsoft-Windows-AppLocker/MSI and Script]
checkpointInterval = 5
current_only = 0
disabled = 0
start_from = oldest
evt_resolve_ad_obj = 1
index=wineventlog
[WinEventLog://Microsoft-Windows-AppLocker/EXE and DLL]
checkpointInterval = 5
current_only = 0
disabled = 0
start_from = oldest
evt_resolve_ad_obj = 1
index=wineventlog
[admon://default]
disabled = true
monitorSubtree = 1
[WinRegMon://hkcu_run]
disabled = 0
hive = \\REGISTRY\\USER\\.*\\Software\\Microsoft\\Windows\\CurrentVersion\\Run\\.*
proc = .*
type = set|create|delete|rename
index = windows
[WinRegMon://hklm_run]
disabled = 0
hive = \\REGISTRY\\MACHINE\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Run\\.*
proc = .*
type = set|create|delete|rename
index = windows
But I don't think that the Problem is related to the Inputs.conf. If I check the Windows Events, I see a TaskCategory Field, but i cannot search for it.