- Splunk Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- How to list multiple fields separately and calcula...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
good afternoon
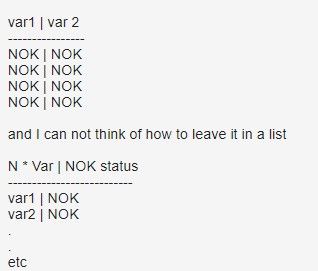
It is possible to group in a variable the state of multiple fields? Currently I have several fields and each one has to fulfill a condition, but if this happens the state NOK must remain
index = "test" sourcetype = "test2"
| stats
max (field1) as field1,
max (field2) as field2
by _time
| eval var1 = if (field1 <9999, "NOK", var1)
| eval var2 = if (field2 <9999, "NOK", var2)
| fields - _time
In this example the values are shown to me this way and many times the NOK value, which only needs 1
Does anybody have any suggestions?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Try like this
Final Answer
..base search
| stats
max (field1) as field1,
max (field2) as field2
by _time
| eval var1 = if (field1 <9999, "NOK", var1)
| eval var2 = if (field2 <9999, "NOK", var2)
| dedup var1 var2
| eval temp=0 | untable temp "N*Var" "NOK Status"
| where 'NOK Status' = "NOK"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Try like this
Final Answer
..base search
| stats
max (field1) as field1,
max (field2) as field2
by _time
| eval var1 = if (field1 <9999, "NOK", var1)
| eval var2 = if (field2 <9999, "NOK", var2)
| dedup var1 var2
| eval temp=0 | untable temp "N*Var" "NOK Status"
| where 'NOK Status' = "NOK"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello
Thank you very much is almost 99% of what I wanted, can you do something similar to this?
| where "NOK Status"! = "OK"
It would only filter the NOK states
Agradesco your answer.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes.. just add | where 'NOK Status'="NOK" to end of above search.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
gracias por todo
Saludos
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Glad to be of help. If there are no further follow-up question related to this, do remember to accept this answer to close the question.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
if I am understanding the question right. I believe what you want to look up is the transpose function it turns columns into rows
https://docs.splunk.com/Documentation/Splunk/7.1.2/SearchReference/Transpose
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Is there some portion of query missing? You're referencing field var1 and var2 in your eval expressions (on RHS of 😃 but they don't exist after your stats command.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
hello, the truth is the query is that but I do not know how to perform the missing part to group the values or make a state dedup and list them