- Splunk Answers
- :
- Using Splunk
- :
- Dashboards & Visualizations
- :
- help for my first chart
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
help for my first chart
Hi
In a Dashboard i use this code for doing a data synthesis
index="wineventlog" sourcetype="wineventlog:*" "Type=Critique" OR "Type=Avertissement" | stats count by Type
i would like to do a pie chart which gives me the percentage of critique and the percentage of avertissement
could you help me please?
thanks
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
sorry i have a last question :
where i put your code in "my" code
YOUR CODE :
- First Chart
- -24h@h
- now
- QA
- index=_internal sourcetype=splunkd log_level=* component!="Metrics"
- | stats count by log_level
- | rename log_level as Type
- $tokTime.earliest$
- $tokTime.latest$
- 1
- 10
- none
- none
- false
- progressbar
- true
- false
- true
- | eventstats sum(count) as Total
- | eval percent=round((count/Total)*100,1)
- | eval Type=Type."(count: ".count.", percent: ".percent.")"
- | fields - count Total
- pie
- 0.0001
- all
- progressbar
- [0x1e93c6,0xf2b827,0xd6563c]
MY CODE :
2.FO_Stopped_Services3.12.55.
5.6.
10.
<panel>
<table>
<title>FO_Stopped_Services_Synthesis</title>
<search ref="FO_Services_Count"></search>
<option name="drilldown">row</option>
<format type="color" field="count">
<colorPalette type="sharedList"></colorPalette>
<scale type="sharedCategory"></scale>
</format>
</table>
</panel>
<panel>
<chart>
<title>FO_Stopped_Services_Chart</title>
<search ref="FO_Chart_Services"></search>
<option name="charting.drilldown">none</option>
</chart>
</panel>
<panel>
<table>
<title>FO_Stopped_BIT_Service</title>
<search ref="FO_Service_BITS"></search>
<option name="count">10</option>
<option name="drilldown">row</option>
<option name="rowNumbers">false</option>
</table>
</panel>
<panel>
<table>
<title>FO_Stopped_PC Services_Service</title>
<search ref="FO_Service_PC Services"></search>
<option name="count">10</option>
<option name="drilldown">row</option>
<option name="rowNumbers">false</option>
</table>
</panel>
<panel>
<table>
<title>FO_Stopped_SCCM_Services</title>
<search ref="FO_Service_SCCM"></search>
<option name="count">10</option>
<option name="drilldown">row</option>
</table>
</panel>
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
i dont know why but this code generate me only 2 label in the chart: SMS Agent Host and Service de Transfert intelligent => YES IT WAS A SLOT TIME ISSUE! NOW IT S OK!
AND NOW I ASLSO UNDERSTAND YOUR HTML CODE
MANY MANY THANKS
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@jip31jip31, glad it worked for you ... Please do Accept the answer I have provided to mark this question as answered and up vote the answers/comments that helped.
| makeresults | eval message= "Happy Splunking!!!"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
First
i use this code for doing a chart report:
index="*" DisplayName="RCAgentMgr" OR DisplayName="SMS Agent Host" OR DisplayName="Service de transfert intelligent en arrière-plan" Started="false" State="Stopped" | stats count by DisplayName | eventstats sum(count) as Total | eval percent=round((count/Total)*100,1) | eval DisplayName=DisplayName."(count: ".count.", percent: ".percent.")" | fields - count Total
i dont know why but this code generate me only 2 label in the chart: SMS Agent Host and Service de Transfert intelligent
Even if in my 3 others report by service, i a m able to collect datas!
and concerning the code you sent me i have difficulties to adapt it
can you confirm me that i have to put this code in UI or source of my Dashboard?
actually i have this code :
First
i use this code for doing a chart report:
index="*" DisplayName="RCAgentMgr" OR DisplayName="SMS Agent Host" OR DisplayName="Service de transfert intelligent en arrière-plan" Started="false" State="Stopped" | stats count by DisplayName | eventstats sum(count) as Total | eval percent=round((count/Total)*100,1) | eval DisplayName=DisplayName."(count: ".count.", percent: ".percent.")" | fields - count Total
i dont know why but this code generate me only 2 label in the chart: SMS Agent Host and Service de Transfert intelligent
Even if in my 3 others report by service, i a m able to collect datas!
and concerning the code you sent me i have difficulties to adapt it
can you confirm me that i have to put this code in UI or source of my Dashboard?
actually i have this code :
2.First Chart3.12.55.
5.6.
10.
<panel>
<table>
<title>FO_Services_Count</title>
<search ref="FO_Services_Count"></search>
<option name="drilldown">none</option>
</table>
</panel>
<panel>
<chart>
<title>FO_Chart_Services</title>
<search ref="FO_Chart_Services"></search>
<option name="charting.drilldown">none</option>
</chart>
</panel>
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
First
i use this code for doing a chart report:
index="*" DisplayName="RCAgentMgr" OR DisplayName="SMS Agent Host" OR DisplayName="Service de transfert intelligent en arrière-plan" Started="false" State="Stopped" | stats count by DisplayName | eventstats sum(count) as Total | eval percent=round((count/Total)*100,1) | eval DisplayName=DisplayName."(count: ".count.", percent: ".percent.")" | fields - count Total
i dont know why but this code generate me only 2 label in the chart: SMS Agent Host and Service de Transfert intelligent
Even if in my 3 others report by service, i a m able to collect datas!
and concerning the code you sent me i have difficulties to adapt it
can you confirm me that i have to put this code in UI or source of my Dashboard?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@jip31jip31 please post code using the code button (101010) on Splunk Answers. Also while posting a command you can click on Add Comment link instead of posting the same as answer.
Can you share the code from one of your other three reports?
With the example I had shared, You should put the query from report in your first search and then reuse the same query in second panel using post processing. That way count should not differ.
| makeresults | eval message= "Happy Splunking!!!"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
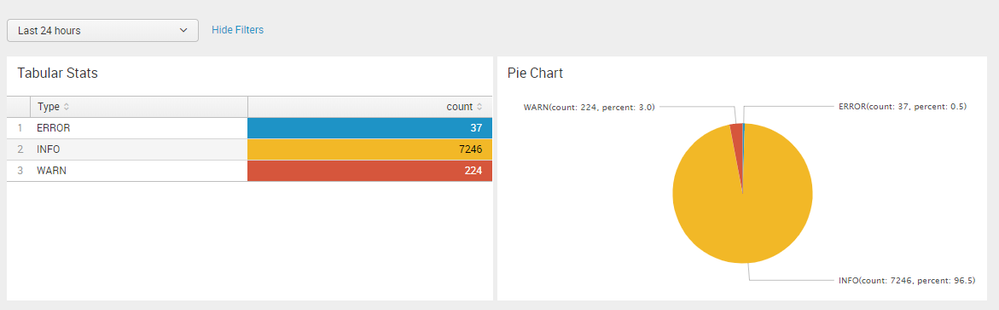
Refer to following run anywhere dashboard which uses post processing to run the same search in two panels. Using Post processing data is fetched from index once and then statistical aggregates are passed over from base search over to the post process search.
Read about Post processing Search documentation including Best Practices: http://docs.splunk.com/Documentation/Splunk/latest/Viz/Savedsearches#Post-process_searches_2
Also if you are learning Splunk Dashboards you should download and try out Splunk Dashboard Examples App from Splunkbase which explains a lot of required concepts with examples.
Please try out and confirm!
<form>
<label>First Chart</label>
<fieldset submitButton="false">
<input type="time" token="tokTime" searchWhenChanged="true">
<label></label>
<default>
<earliest>-24h@h</earliest>
<latest>now</latest>
</default>QA
</input>
</fieldset>
<row>
<panel>
<title>Tabular Stats</title>
<table>
<search id="baseSearchStats">
<query>index=_internal sourcetype=splunkd log_level=* component!="Metrics"
| stats count by log_level
| rename log_level as Type</query>
<earliest>$tokTime.earliest$</earliest>
<latest>$tokTime.latest$</latest>
<sampleRatio>1</sampleRatio>
</search>
<option name="count">10</option>
<option name="dataOverlayMode">none</option>
<option name="drilldown">none</option>
<option name="percentagesRow">false</option>
<option name="refresh.display">progressbar</option>
<option name="rowNumbers">true</option>
<option name="totalsRow">false</option>
<option name="wrap">true</option>
<format type="color" field="count">
<colorPalette type="sharedList"></colorPalette>
<scale type="sharedCategory"></scale>
</format>
</table>
</panel>
<panel>
<title>Pie Chart</title>
<chart>
<search base="baseSearchStats">
<query>| eventstats sum(count) as Total
| eval percent=round((count/Total)*100,1)
| eval Type=Type."(count: ".count.", percent: ".percent.")"
| fields - count Total</query>
</search>
<option name="charting.chart">pie</option>
<option name="charting.chart.sliceCollapsingThreshold">0.0001</option>
<option name="charting.drilldown">all</option>
<option name="refresh.display">progressbar</option>
<option name="charting.seriesColors">[0x1e93c6,0xf2b827,0xd6563c]</option>
</chart>
</panel>
</row>
</form>
| makeresults | eval message= "Happy Splunking!!!"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
i havent enough karma to send screenshot....
you can open it at https://cjoint.com/c/HDciQyZZJUi
thanks
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@jip31jip31, splunk answers has an Image button (shortcut CTRL+G) which will allow you to paste the web link to attach image to your comment/answer.
You have to make sure your stats query in searches for stats table and pie chart are the same. Also that Splunk input tokens (in your case Time) is being passed to both the panels. One of the options would be to create a base search for your first stats table and then use the same search in your pie chart as post process search. This will also improve performance and ensure that same search runs for both panels.
Please refer to my answer with Run Anywhere Example based on Splunk's _internal index for you to test and confirm.
| makeresults | eval message= "Happy Splunking!!!"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello and thanks
i succeed to do my fits pie chart 🙂
but there is Something very stranhe
in my count report i have to 3 entrie :
RCAgentMgr 11
SMS Agent Host 288
Service de transfert intelligent en arrière-plan 1418
But in the chart i havent the entrie "RCAgentMgr" and for the entrie Service de transfert intelligent i have the same number of events!
do you have an idea please???
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@jip31, can you add a screenshot? Do you see OTHERS slice instead of RCAgentMgr in the pie chart?
You can add the following to Simple XML chart configuration to your dashboard to reduce the threshold to collapse Pie Slices to OTHERS category. You can do the same from UI Edit > Format Visualization option as well.
<option name="charting.chart.sliceCollapsingThreshold">0.0001</option>
| makeresults | eval message= "Happy Splunking!!!"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
So When you run above search and select Pie chart in the visualization tab, you don't get a chart? Is Type already exist as field?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sorry but for m'y first chart it doesnt help me...
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@jip31, I have updated my answer please try out.
| makeresults | eval message= "Happy Splunking!!!"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
[Updated Answer]
Try the following query with visualization as Pie Chart:
index="wineventlog" sourcetype="wineventlog:*" "Type=Critique" OR "Type=Avertissement"
| stats count by Type
| eventstats sum(count) as Total
| eval percent=round((count/Total)*100,1)
| eval Type=Type."(count: ".count.", percent: ".percent.")"
| fields - count Total
If you are creating Pie Chart for the first time refer to Splunk Documentation: https://docs.splunk.com/Documentation/Splunk/latest/Viz/PieChart
@jip31, refer to one of my older answer for a similar question https://answers.splunk.com/answers/591290/pie-chart-round-default-percentage.html
| makeresults | eval message= "Happy Splunking!!!"