- Splunk Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- How to validate regex expression?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
my regex:
s/[^a-z]+\d/####/g
Output:
/v3/securemessages/members654fdfgd2-b2ad545a-b2f2-d545eb545d45/messages/incident4545/reply
Expected output:
/v3/securemessages/members/messages/incident/reply
please help on this.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
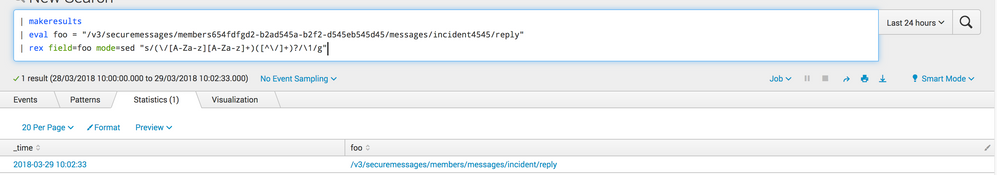
As I mentioned above, try the following regex:
| rex field=yourfield mode=sed "s/(\/[A-Za-z][A-Za-z]+)([^\/]+)?/\1/g"
For example, if I replicate your example in my lab:
| makeresults
| eval foo = "/v3/securemessages/members654fdfgd2-b2ad545a-b2f2-d545eb545d45/messages/incident4545/reply"
| rex field=foo mode=sed "s/(\/[A-Za-z][A-Za-z]+)([^\/]+)?/\1/g"
Output:
Hope that helps.
Thanks,
J
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
As I mentioned above, try the following regex:
| rex field=yourfield mode=sed "s/(\/[A-Za-z][A-Za-z]+)([^\/]+)?/\1/g"
For example, if I replicate your example in my lab:
| makeresults
| eval foo = "/v3/securemessages/members654fdfgd2-b2ad545a-b2f2-d545eb545d45/messages/incident4545/reply"
| rex field=foo mode=sed "s/(\/[A-Za-z][A-Za-z]+)([^\/]+)?/\1/g"
Output:
Hope that helps.
Thanks,
J
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks J
When i used the regex i am getting output like this
/v3/securemessages/members/a#####aae#####b#####e-ae#####e#####aa#####f/categories
Because I have lot URI in my event
so i have query like this below:
index=test_prod| rex field=URI "^(?.+?)(\?|\z)"
| rex field=APIName mode=sed "s/[0-9A-F]{32}/#####/g"
| rex field=APIName mode=sed "s/[0-9]{7}[\w]{2}[\d]{4}/#####/g"| rex field=APIName mode=sed "s/[^a-z]+\d/#####/g"| rex field=APIName mode=sed "s/[0-9]+\d/#####/g" |rex field=APIName mode=sed "s/(\/[A-Za-z][A-Za-z]+)([^\/]+)?/\1/g"
| stats count by APIName Sender
Can you please help on this
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
What do you want to see instead of
/v3/securemessages/members/a#####aae#####b#####e-ae#####e#####aa#####f/categories
All the rex's you are running there in SED mode are basically replacing every match with 5 hashes so if you don't want to see that you can simply leave the second part of your SED pattern empty, as in:
| rex field=APIName mode=sed "s/[0-9A-F]{32}//g"
| rex field=APIName mode=sed "s/[0-9]{7}[\w]{2}[\d]{4}//g"
| rex field=APIName mode=sed "s/[^a-z]+\d//g"
| rex field=APIName mode=sed "s/[0-9]+\d//g"
But it all looks over complicated to me so again, if you can provide a detailed sample, how it looks initially and your desired output, I might be able to help more.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks a lot
There is lot of URL i will send some complicated URI
/v1/utility/hcpcsprocedurecodes/j7q
/v1/utility/hcpcsprocedurecodes/m
/v1/utility/hcpcsprocedurecodes/m7zv
/v1/utility/hcpcsprocedurecodes/m7zz
/v1/utility/revenuecodes/m
/v1/utility/revenuecodes/m7zv
/v3/securemessages/members/afae0-a4ecae9be1/categories
/v3/securemessages/members/afbfc-a7d3-f4afedf/categories
/v3/securemessages/members/bda8eaaa-bdaf1e/messages/incident/reply
Have to remove ' bda8eaaa-bdaf1e','afbfc-a7d3-f4afedf'
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
can you try this:
...|rex mode=sed "s/^((\/\w+){2})(\/\D+).*?(\/\w+\/\D+).*?(\/\w+)/\1\3\4\5/g"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
try this,
.+((?i)members\/).+
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@karthi2809, what exactly are you trying to achieve if I may ask?
Do you simply want to get rid of the numbers and symbols from any directory level in your path?
If so, what about v3, does that count too?
See in any case my answer below in case it helps.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
|rex mode=sed "s/^((\/\w+){2})(\/\D+).*?(\/\w+\/\D+).*?(\/\w+)/\1\3\4\5/g"