- Splunk Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- How to write regex to select specific fields on a ...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
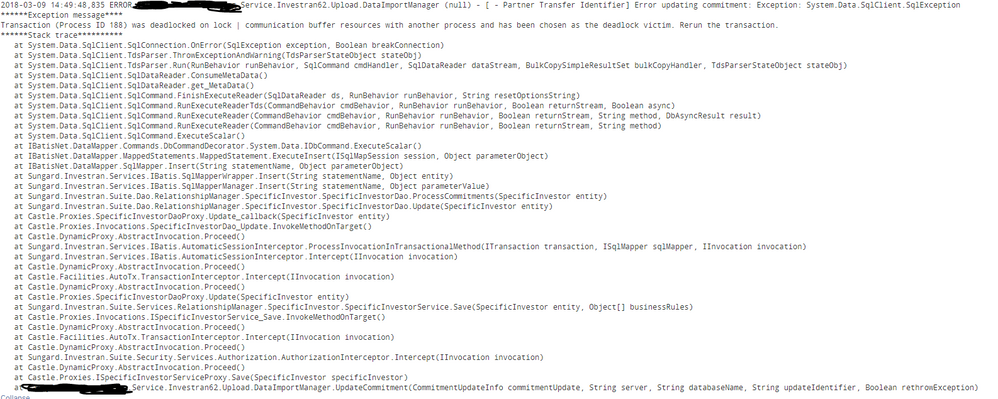
hi below is my search,
when I do search for Error this is what I get;
then I run this search to create "Message" field and it brings up from ERROR to ***Exception message*
index=pa host=aptr45 sourcetype=Service| transaction startswith="Error" endswith="ERROR" maxevents=15000 | rex "ERROR (?.*)"|table host,Message,_time
I basically want to bring everything starting from ERROR to all the way down to the last line. How do I do that?
I also wanted to extract another field starting from **Exception message** to ***Stack Trace* but it doesn't work.any help is appreciated.
for that, I tried using multiple combinations and I was not successful. i tried using; |rex " Exception message (?.Stack trace)", |rex " *Exception message* (?.*Stack trace)", |rex " Exception message (?.*)",
I tried using field extractor to address the issue but I guess it was to complex that it kept giving me error while trying to extract it.
I've never written regex manually before so please be patient with me:)
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
A most excellent resource for writing regular expressions is regex101.com. There you can paste some sample data then try various regex strings to see what matches.
To get Splunk to match text across lines, use [\s\S]* instead of .*. So your first search would become index=pa host=aptr45 sourcetype=Service| transaction startswith="Error" endswith="ERROR" maxevents=15000 | rex "ERROR (?<foo>[\s\S]*)"| table host,Message,_time.
If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
A most excellent resource for writing regular expressions is regex101.com. There you can paste some sample data then try various regex strings to see what matches.
To get Splunk to match text across lines, use [\s\S]* instead of .*. So your first search would become index=pa host=aptr45 sourcetype=Service| transaction startswith="Error" endswith="ERROR" maxevents=15000 | rex "ERROR (?<foo>[\s\S]*)"| table host,Message,_time.
If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you richgalloway.i will definitely check regex101.
quick question if i wanted to extract 2 fields,first one would be the lines starting from Error to *Exception Message* and second would be the lines between **exception message to the the last line what would be the search look like.thanks for all the help
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
That's probably best done with two rex commands.
index=pa host=aptr45 sourcetype=Service| transaction startswith="Error" endswith="ERROR" maxevents=15000 | rex "ERROR (?<foo>[\s\S]*)"| rex "ERROR (?<bar>.*)" | table host,Message,_time
If this reply helps you, Karma would be appreciated.