- Splunk Answers
- :
- Using Splunk
- :
- Splunk Dev
- :
- correlate 2 events with uid in a table
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
I want information about the usb keys mounted on the system but the / var / log / messages or the /var/log/audit/audit.log do not give enough interesting information about the USB sticks.
So I want to use the data contained in the / etc / passwd and the / etc / mtab to correlate the information and thus deduce in a table the login of the current session and the name of the usb key mounted on it.
I used the add-on unix to generate the information contained in the / etc / passwd but this add-on does not propose me to generate the information of / etc / mtab, so I configured splunk for it to monitor this file and since this file is dynamic, when a line is added at the end of the file when we insert a usb key, this line is automatically generated on splunk.
Now I want to find a way to correlate message 1 with message 2.
I want to correlate the uid ie in the message 1 we see that there is the uid 500, so I will use the message 2 to deduce that 500 = local_splunk. After correlating the uids I want to make a table that will show me the uid, user, usb key name mounted.
Thank you
Amir
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Something like that but the field user is empty:
Thank you
Amir
**PS: I'm going to leave soon because it's getting late and I'll be back to work next Monday because I'm at school at the end of the week. From my return Monday, I continue on that so if I do not answer it is just because I will not be there.
Thank you very much for your help.**
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@elliotproebstel,
I think this time, I found the request that I needed and with the time and date thank you for your help.
sourcetype="mtab_executer" OR source="unix:useraccounts"
| rex max_match=0 "(^|\n)(?<usb_key>\/\S+\s\/\S+)"
| eval user_id=coalesce(user_id, uid)
| eventstats latest(user) AS user BY user_id
| convert timeformat="%H:%M:%S" ctime(_time) AS c_time
| stats latest(c_time) AS Time, latest(user) AS user, latest(user_id) AS user_id, count BY usb_key
Result:
Amir
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Something like that but the field user is empty:
Thank you
Amir
**PS: I'm going to leave soon because it's getting late and I'll be back to work next Monday because I'm at school at the end of the week. From my return Monday, I continue on that so if I do not answer it is just because I will not be there.
Thank you very much for your help.**
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sure thing, although I don't quite understand what you're representing when you have a timestamp on the same line with the count. Presumably, that usb_key wasn't seen 1936 times at a single moment - so you might give some thought to what that communicates. But certainly you know your intentions better than I do.
I think this should do it:
your base search
| rex max_match=0 "(^|\n)(?\/\S+\s\/\S+)"
| eval user_id=coalesce(user_id, uid)
| eventstats latest(user) AS user BY user_id
| eval usb_time=if(source="/etc/mtab", _time, NULL)
| stats latest(usb_time) AS _time, list(user) AS user, list(user_id) AS user_id, count BY usb_key
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello @elliotproebstel,
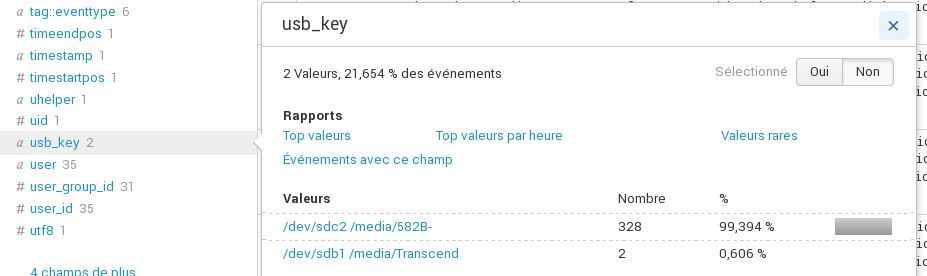
I have 1936 times the usb_key Transcend and 2207 times others usb_key because I did tests with Transcend that was not mounted and the other keys that were.
Amir
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
i want to know how can i correlate uid of the message 1 with the uid in the message 2 and deduct the user and display the event when it appears with the names of the usb keys that I extracted. Because i have i problem which is, when event appear splunk only takes the usb key events alone and does not correlate the uid in the event with the uid of the message 2. is there not a function that basically allows to set up a dynamic array or when the 'event 1 appears it will directly dig into it and deduce that uid 500 = local_splunk.
Still sorry for the double post
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
sorry but i want to add the time in the table but when i add it the user field becomes empty as if the correlation was no longer working.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sure. Given the events above, do you want to use the time from the event that contained the name of the USB key? If so, I'd do this:
your base search
| rex max_match=0 "(^|\n)(?<usb_key>\/\S+\s\/\S+)"
| eval user_id=coalesce(user_id, uid)
| eval usb_time=if(source="/etc/mtab", _time, NULL)
| stats latest(usb_time) AS _time, list(user) AS user, list(usb_key) AS usb_key BY user_id
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
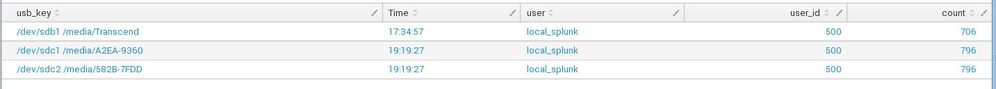
is it possible to display this by usb key with the number of times they appear each and uid and the user and the date ?
thank you
Amir
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@elliotproebstel,
yes, please.
I did this for now but I can only get the first 2 usb key not the 3:
my search | rex "(\n)(?<usb_key>/\w+/\w+\s+/\w+/\w+[-\w+])"
In the picture after, there is my event which i want use:
And what i extract with my rex:
Thank you
Amir
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Does this work?
| rex "^(?<usb_key>\/\S+\s\/\S+)"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
yes, it works for the first line /dev/sdb1 /media/Transcend but not for the 2 others.
it's well extracted to /dev/sdb1 /media/Transcend
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
but my main problem is to extract the 2 from below.
Sorry for the double post.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Got it. Does this work for you?
| rex "(^|\n)(?<usb_key>\/\S+\s\/\S+)"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
it is the same problem it works but with the first line.
it extract me /dev/sdb1 /media/Transcend but not the 2 others.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Ahh, I was forgetting the max_match option, which may be biting us. Sorry for shooting in the dark a bit here, but I don't have access to a Splunk instance at the moment, so I can't test things before posting. I'm going to shotgun several options here, and you can test any/all of them:
First:
| rex max_match=0 "(?s)(?<usb_key>\/\S+\s\/\S+)"
Second:
| rex max_match=0 "(^|\n)(?<usb_key>\/\S+\s\/\S+)"
Third:
| rex max_match=0 "[\S\s](?<usb_key>\/\S+\s\/\S+)"
I'm hoping one of these works!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It's not a problem that, you take your time to help me on the contrary I'm happy to learn.
the first 2 are good, I have the 3 that are extracted.
Is it possible that you explain:
rex max_match = 0 "(^ | \ n) (? <usb_key> \ / \ S + \ s \ / \ S +)" and [\ S \ s] which is in the 2nd expression.
thank you
Amir
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Great! And I'm happy to explain!
The snippet (^|\n) in the first is looking for ^, which means the start of the line OR \n, which is a newline character. I was figuring that the first line wouldn't be preceded by a newline, so we'd need ^ to grab the first one.
The [\S\s] was also a bit of a trick to look for any character at all (including a newline), because it matches on \S (any non-whitespace character) or \s (any whitespace character). But I expect it probably failed to grab the first line, since the first usb_key value had nothing at all before it. It might work if revised like this:
| rex max_match=0 "[\S\s]?(?<usb_key>\/\S+\s\/\S+)"
because that makes the [\S\s] optional (zero or one matches will pass).
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
ok thank you so much for your help @elliotproebstel .
I learned a lot today 🙂
Amir
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
My pleasure!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If you already have the usb key name extracted into a field called usb_key, then this should work:
your current search
| eval user_id=coalesce(user_id, uid)
| stats list(user) AS user, list(usb_key) AS usb_key BY user_id