- Splunk Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- How to Extract "String" as value using "+Extract N...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How to Extract "String" as value using "+Extract New Fields" feature
Hi,
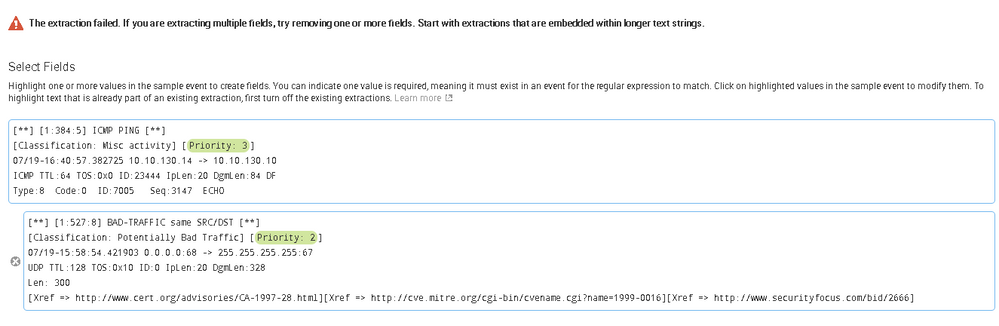
I have some snort logs with prior 0,1,2,3. I used the extract new fields feature to extract the priority value as a priority field and did a pie chart by searching snort | top priority but my chart will end up show just values 0,1,2 or 3.
I noticed that if I used the default fields that were non values like ip addresses, the chart actually could display by field names. Then I tried to extract another new field but selecting the string "Priority : 3" as newPriority but the field summary only shows newPriority cound as 1 x "Priority 3".
How do I extract a field like the IP field where it treat 192.168.1.1 and 192.168.1.2 as 2 different value in IP field?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
As per the query you posted, here is the possible solution I managed to get which you can follow-
- Open your snort logs in the tool or platform you are using for log analysis.
- Look for a feature or option that allows you to define custom extraction rules or create new fields based on the log data. This may vary depending on the specific tool you are using.
- Find the option to add a new field or define a custom extraction rule. Name the new field "Priority" or any desired name.
- Specify the extraction rule for the "Priority" field. In this case, you want to extract the string value.
- Depending on the tool, you may need to provide a regular expression or a pattern that matches the desired string. For example, you could use a pattern like Priority : (\d) to capture the priority value. Adjust the pattern as per your specific log format.
- Save the new field or extraction rule.
- Apply the newly created "Priority" field to your log analysis or visualization. Depending on the tool, you may need to re-run the analysis or refresh the visualization.
- Once the "Priority" field is applied, you should be able to generate a pie chart by searching for snort | top Priority. This should display the different priority values as distinct slices in the chart.
By defining a custom extraction rule or field (https://docs.splunk.com/Documentation/Splunk/9.1.0/Data/Configureindex-timefieldextraction) for the priority value, you can ensure that it treats different values, such as "Priority : 3" and "Priority : 2", as separate entities rather than merging them into a single value.
Note: The specific steps may vary depending on the log analysis tool or platform you are using. Please consult the documentation or support resources for your specific tool for more accurate instructions tailored to your environment. Also, this Splunk certification resource will help you understand it more better.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
I mean I wanted my field to be in Fields » Field extractions so that when I search sourcetype, I can see it as a field and straight away know how many priority 1,2,3,4 as a quick preview. Not by SPL.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Here are the most important rules for searching in Splunk:
Search terms are case insensitive.
You can combine multiple search terms in a single search.
To search for a phrase, use quotation marks. For example, to search for an exact phrase of failed login, you would enter “failed login” in the search bar.
Boolean logic is supported. You don’t have to write the AND keyword between search terms; it is implied. To specify that either one or two or more arguments should be true, use the OR keyword. To filter out events containing a specific word, use the NOT keyword.
Splunk’s search language is known as the Search Processing Language (SPL). This language contains hundreds of search commands and their functions, arguments, and clauses. For example, to sort results in either ascending or descending order, you would use the SPL command sort. To format results into a tabular output, you can use the table command. Learn More Here...