- Splunk Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- How to create a new key-value pair from various fi...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
my events can include a fieldname with a pattern like:
product_type_a
product_type_b
product_type_c
To group calculations by product type, I think about creating a new key-value pair like
type=product_type_A. I could use a CASE command, but then I need to know all product_type_* that will appear in the future.
Is there a way to use something like COALESCE in combination with a wildcard or LIKE, to grab the first appearing fieldname as value?
Thanks in advance
Heinz
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Like this:
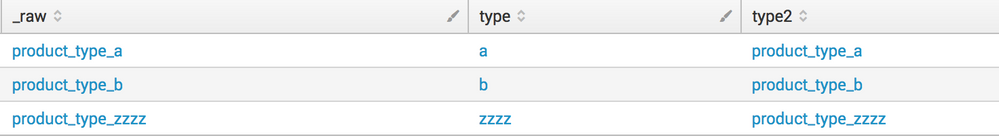
| rex max_match=1 "(?<type>product_type_\w+)"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I tried that out but the search shows an error:
Error in 'SearchOperator:regex': Usage: regex (=|!=)
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I had a typo! I meant rex, not regex! Try the fixed answer now!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I'm not sure if I understand completely what your request is. Are you saying Splunk is extracting different product names from your events as their own individual fields? Could you provide a few samples of your events, and a screen shot? I may be able to help, but I'd need to see the data first.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I would like to extract a new key value pair from fieldnames that can appear in the events.
Let's say we have 3 events, with these fieldnames and amounts.
event1: product_type_a=5
event2: product_type_b=8
event:3 product_type_c=10
What I want to do here, is to transform fieldnames with the pattern product_type_* into values for the new field "type". So in the end, I have a new field per event
event1: type=product_type_a
event2: type=product_type_b
event3: type=product_type_c
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi HeinzWaescher,
could you detail your question?
you can group events by type using stats command, but you already know!
if you want, you could also populate a lookup with a scheduled search and list all the type values to use in your statistic searches.
Bye.
Giuseppe