- Splunk Answers
- :
- Splunk Premium Solutions
- :
- Security Premium Solutions
- :
- Splunk Enterprise Security
- :
- Why eStreamer data from sourcefire is not getting ...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Why eStreamer data from sourcefire is not getting tagged for IDS_Attacks datamodel?
Hi,
We are indexing eStreamer logs from sourcefire and have the app, "eStreamer for Splunk" (2.2.1) and add-on, "Splunk Add-on for Cisco FireSIGHT" ( 3.3.2) installed on both Indexer and the Search-heads.
But when searching for sourcetype=eStreamer, I do not see any tags getting added to the events. no eventtypes either. As per the Add-on documentation, IDS events should be tagged as "ids" & "attack".
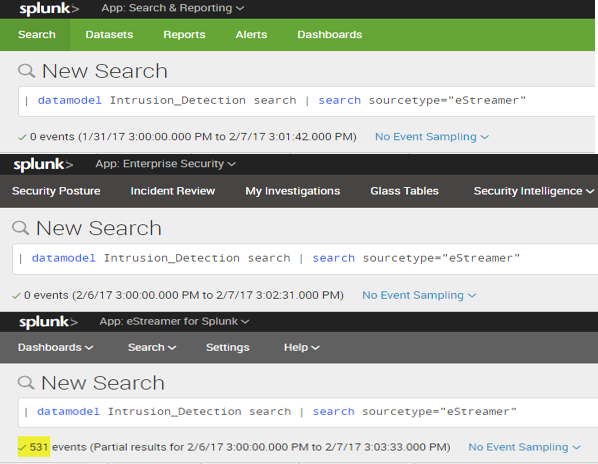
Also, the following query against the Data model does not return any results.
| datamodel Intrusion_Detection IDS_Attacks search | search sourcetype="eStreamer"
I do see that few fields are correct as per CIM, e.g. ides_type, but not all.
e.g. data still returns with dest_ip instead of dest. This is despite the following fieldalias object being present.

Are we missing any additional setting/configuration or Am i searching the datamodel in a wrong way?
Any help would be appreciated.
Many Thanks,
~ Abhi
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You can go to permissions [ via Manage Apps and selecting the estreamer app] and give read/write permissions to required roles and 'tick' All Apps under 'sharing for config file-only objects. This will make all knowledge objects global and ES and search app will be able to use it.
Also, if you want ES to specifically use it, you need to update etc/apps/SplunkEnterpriseSecuritySuite/local inputs.conf's regex to include "eStreamer"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
A new Splunk Firepower solution is now available if you are using Firepower version 6.x. You can download the new eStreamer eNcore for Splunk and the separately installable dashboard from the two links below:
eStreamer eNcore
https://splunkbase.splunk.com/app/3662/
eNcore Dashboard
https://splunkbase.splunk.com/app/3663/
It is free to use and well documented but if you would like to purchase a TAC Support service so that you can obtain installation and configuration assistance and troubleshooting you can order the software from Cisco (support obligatory with this purchase). The Product Identifier is: FP-SPLUNK-SW-K9.
Regardless of whether you take up the support option or not, updated versions will be made available to all free of charge and posted on Splunkbase as well as Cisco Downloads.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi ArtS95147,
Thanks for the comment. Can you please review the comment I just posted?
Changing permissions on these objects might resolve the issue but I am not sure if that is the correct way to go. Should I clone all objects instead or just change the permissions for the existing ones?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Please ask others about the permission issue -- regards.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I believe to have found the problem.
It appears that both tags and eventtypes are working as expected, but the ones which came with the eStreamer app have permissions set to the app(eStreamer) only. This must be the reason why neither "search & reporting" nor "Enterprise Security" apps could search the eStreamer data against the data model.
Also, some of the field aliases required by the model are only in eStreamer app and not in the add-on(permissions for objects within the addon are global, but do not help towards the data model)
I can try changing the permissions for these objects under "eStreamer" app from App only to Global and that should allow other apps like ES to make use of these tags/eventtypes, but not sure if that is the suggested way to resolve this issue.
Any suggestions?