- Splunk Answers
- :
- Splunk Premium Solutions
- :
- Security Premium Solutions
- :
- Splunk Enterprise Security
- :
- Splunk Enterprise Security: How to pass a token wi...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Splunk Enterprise Security: How to pass a token with double quotes to a correlation drilldown search?
Assuming I defined a correlation search in Splunk Enterprise Security as the following:
index="_internal" sourcetype="splunkd" log_level="INFO" | stats count by name message | rename name AS "alert name"
How can I pass the token "alert name" to the drilldown search?
Thanks.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have been looking over some previous questions like this and I am running into the same issues you have encountered. I am trying to understand where you are trying to get at the end of the day though.
I realize your example search is very generic, but why are you looking to rename that value to a multi word value? Is that associated with how you want it to be shown on the Incident Response page? If so, could that be solved in a different manner in the ES Config - Incident Review Settings - Incident Review Field Attributes?
That way the drill down could stay as search index=Internal $name$ as you have in the example, but the display would show Alert Name when you expand the notable event.
That may not be where you are going with this but figured I would throw that out.
Hope this helps...
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Assuming you want to drilldown when you click on any rows of your search results, you can try as suggested in below sample/runanywhere dashboard.
<form>
<label>ForTest_Delete</label>
<row>
<panel>
<table>
<title>Fired Alerts - token=$alertname$</title>
<search>
<query>index=_internal sourcetype=scheduler status=success alert_actions=summary_index | stats count by savedsearch_name | rename savedsearch_name as "Alert Name"</query>
<earliest>-15m</earliest>
<latest>now</latest>
</search>
<option name="wrap">true</option>
<option name="rowNumbers">false</option>
<option name="drilldown">row</option>
<option name="dataOverlayMode">none</option>
<option name="count">10</option>
<drilldown>
<set token="alertname">$row.Alert Name$</set>
</drilldown>
</table>
</panel>
</row>
</form>
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
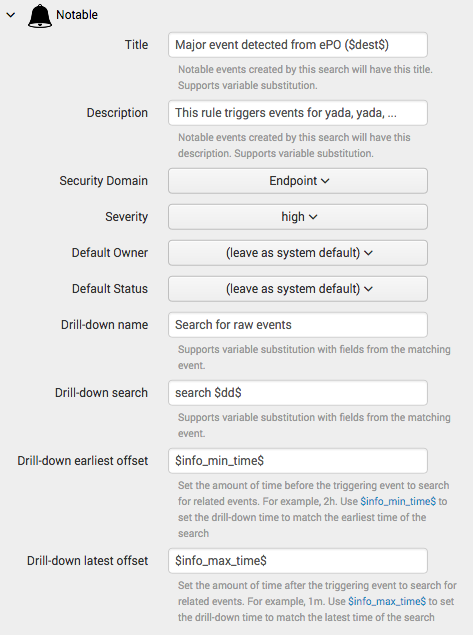
Hi somesoni2, thank you for your information. However, this is related to the correlation search from Splunk Enterprise Security (app), and it is not related to dashboard creation. Please see "Drill-down search" (field) from the image below:
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It says "Supports variable substitution with fields from the matching event", so have you tried using search $alert name$?? Or search %alert name% ?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It doesn't work in either format.
