- Apps and Add-ons
- :
- All Apps and Add-ons
- :
- Why am I getting DateParserVerbose warnings althou...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
I'm forwarding CSV files to Splunk. The timestamp for each event in a file should be set to the file's modtime, therefore I've set DATETIME_CONFIG = NONE for the sourcetype in the props.conf on the indexer. This seems to work, but I'm getting lots of the following warnings:
WARN DateParserVerbose - Failed to parse timestamp. Defaulting to timestamp of previous event (Sat Apr 20 02:39:10 2013). Context: source::D:\LogFiles\2016-09\16-09-30\2016-09-30-10-31-Values.amf|host::MY_HOST|Application Metrics|112033
WARN DateParserVerbose - A possible timestamp match (Mon Sep 24 17:04:52 2007) is outside of the acceptable time window. If this timestamp is correct, consider adjusting MAX_DAYS_AGO and MAX_DAYS_HENCE. Context: source::D:\LogFiles\2016-09\16-09-30\2016-09-30-10-30-Values.amf|host::MY_HOST|Application Metrics|111934
(131364 events produce 1694 warnings)
Why is Splunk trying to find/parse a timestamp? I thought DATETIME_CONFIG = NONE disables the date parser? Is it possible to disable the date parser (for a specific sourcetype)?
Issue occurs on a distributed system (6.4.3) and on a standalone Splunk instance (6.5.0).
EDIT
The props.conf on the forwarder:
###############################################################################
[Application Metrics]
###############################################################################
category = MyApp
description = Application Metrics (*.amf).
pulldown_type = true
# Parsing Phase ###############################################################
CHARSET = UTF-8
INDEXED_EXTRACTIONS = csv
FIELD_DELIMITER = ,
FIELD_HEADER_REGEX = ^\s*[kK]ey\s*,
PREAMBLE_REGEX = ^\s*#
props.conf on the indexer:
###############################################################################
[Application Metrics]
###############################################################################
category = MyApp
description = Application Metrics (*.amf).
pulldown_type = true
# Parsing Phase ###############################################################
DATETIME_CONFIG = NONE
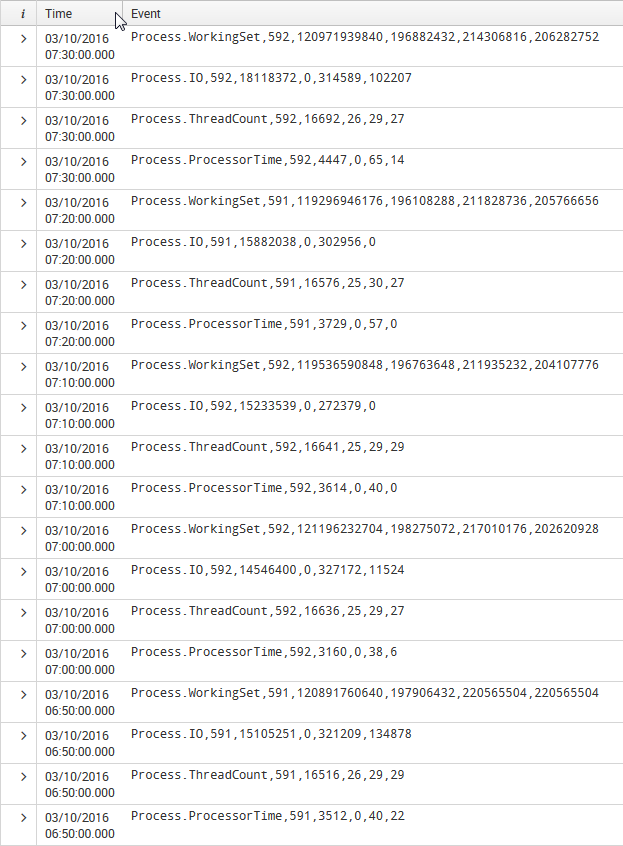
Events around the time at which the warnings are logged:
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Try setting: DATETIME_CONFIG = CURRENT on the forwarder since you are using indexed_extractions
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Try setting: DATETIME_CONFIG = CURRENT on the forwarder since you are using indexed_extractions
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for the reply,
I'll try that. Should I change the props.conf on the indexer as well?
Does DATETIME_CONFIG even influence the forwarder's behavior? Looking at http://wiki.splunk.com/Community:HowIndexingWorks it seems like it is only used by the indexer.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You can remove that on the indexer as indexed extractions are done on the forwarder props.conf.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We moved DATETIME_CONFIG = NONE from the props.conf on the indexer to the forwarder props.conf and it works like a charm. Thanks for pointing that out!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
PERFECT. Please upvote my answer and have a nice day.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Include a sample of some events, include your props.conf so we can comment properly. Thanks!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I've updated my question (added props.conf and a screenshot showing resulting events).