- Splunk Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- how to compare values from two different searches
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
how to compare values from two different searches
Hi,
I need to run a compare against the count of two different searches - how would I do that? I'm counting the number of unique sources from two different indexes, and they need to be the same.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi a212830,
Read https://answers.splunk.com/answers/129424/how-to-compare-fields-over-multiple-sourcetypes-without-jo... and watch the March 2016 virtual.conf talk from http://wiki.splunk.com/Virtual_.conf for more info how this can be done.
Hope this helps ...
cheers, MuS
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I like the elegance of using OR and I will have to revisit some old searches.
Would this work for the op's scenario where they want a distinct count of events in two different indexes?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
of course:
index=_internal OR index=_audit
| eval internal_count=if(index="_internal", 1, null())
| eval audit_count=if(index="_audit", 1, null())
| stats sum(internal_count) AS internal sum(audit_count) AS audit
| eval diff=internal-audit
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How would you do that for comparing the count of two sourcetypes in one index?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Ah, got that figured out. And using your technique you can do it across two as well. Cool!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
That's so awesome! TYVM!!!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
A simple stats command should do the trick
index=index1 OR index=index2 | stats dc(source) by index
Have a read http://docs.splunk.com/Documentation/Splunk/6.3.3/SearchReference/Stats
If theres one command you learn, make it stats!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It depends upon what type of searches and what columns are available on those two searches. Could you provide some more information on the output of the those two searches? Based on that it could be appendcols OR join OR may be simple stats can do the job.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
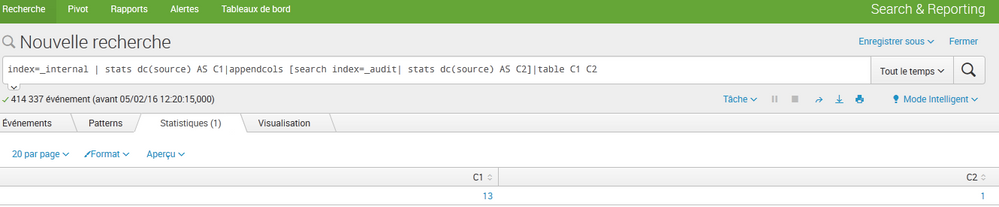
index=index1 | dedup source | stats dc(source) AS idx1ct | appendcols [search index=index2 | dedup source | stats dc(source) AS idx2ct ] | eval nodiff=if(match(idxct1,idxct2),"True","False") | table nodiff
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I guess you should be using appendcols here. Append will create those fields in totally different events/rows and your eval will fail.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
changed to appendcols, thanks. So a little more explanation now that I'm not on my phone. The search creates a field called nodiff that is true if there isnt a difference in the count of sources between indexes, or false if there is a difference. The dedups speed up the stats distinct count functions but are not required. Remove the final table to see the rest of the fields.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks!!!!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If this answered your question can you mark it as the answer please?
Also see MuS's answer below. Apparently it is more efficient than appendcols. If you find that the search is faster or more reliable using his technique, then please mark his as the answer.