Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Splunk Enterprise Security
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- Splunk Answers
- :
- Splunk Premium Solutions
- :
- Security Premium Solutions
- :
- Splunk Enterprise Security
- :
- Splunk App for Enterprise Security: Empty csv look...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
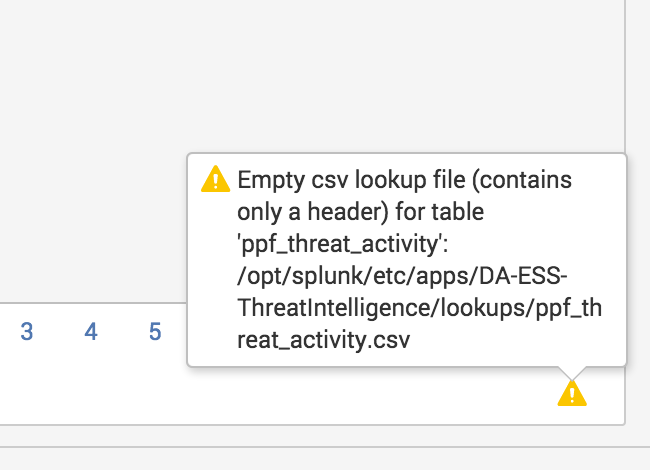
Splunk App for Enterprise Security: Empty csv lookup file (contains only a header) for table ppf_threat_activity
mcronkrite

Splunk Employee
09-08-2015
07:07 PM
New install of ES 3.3, the populating search appears not to have run... How can I jump start this lookup?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
DMohn
Motivator
02-25-2016
06:26 AM
This lookup gets populated, if you use the "Advanced Filter" on the Thread Activity Dashboard. Select one (or more) events in the Thread Activity Details Panel, and filter or highlight the events. This will add an entry in the ppf_thread_activity.csv lookup.
If you don't want to use this functionality, you could also highlight and unhighlight the event, which will still create an entry in the csv, and make the warning disappear - but no highlights will remain!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
jeremycarterdhs
Explorer
12-29-2016
10:14 AM
Thank you for the answer. I love when it's a simple fix!
Get Updates on the Splunk Community!
Stay Connected: Your Guide to May Tech Talks, Office Hours, and Webinars!
Take a look below to explore our upcoming Community Office Hours, Tech Talks, and Webinars this month. This ...
They're back! Join the SplunkTrust and MVP at .conf24
With our highly anticipated annual conference, .conf, comes the fez-wearers you can trust! The SplunkTrust, as ...
Enterprise Security Content Update (ESCU) | New Releases
Last month, the Splunk Threat Research Team had two releases of new security content via the Enterprise ...