- Apps and Add-ons
- :
- All Apps and Add-ons
- :
- Re: Getting error message in CSV header field and ...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Getting error message in CSV header field and not date (Splunk_TA_windows v8.2.0)
When running a search for"EventCode=35" OR "EventCode=36" OR "EventCode=37" OR "EventCode=38" source="WinEventLog:System" and then exporting that to a CVS file, column N through BN has the following message as its column header, where <workstation> is the workstation name:
If_this_is_the_first_occurrence_of_this_event_for_the_specified_computer_and_account__this_may_be_a_transient_issue_that_doesn_t_require_any_action_at_this_time___If_this_is_a_Read_Only_Domain_Controller_and__<workstation>___is_a_legitimate_machine_account_for_the_computer__<workstation>__then__<workstation>__should_be_marked_cacheable_for_this_location_if_appropriate_or_otherwise_ensure_connectivity_to_a_domain_controller__capable_of_servicing_the_request__for_example_a_writable_domain_controller____Otherwise__the_following_steps_may_be_taken_to_resolve_this_problem
I am told by the AD team that at leaset Column N should be a date. Starting at column CC and going through EC, I am seeing this as the header:
Otherwise__assuming_that__<workstation>___is_not_a_legitimate_account__the_following_action_should_be_taken_on__<workstation>_
These headers are no where to be found when the search brings back data. they only show up when exporting to CSV.
Anyone have any idea what is going on?
______
Edited to add: I also want to point out this only happen when searching in Smart or Verbose Mode. it does not happen in Fast mode.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You probably want to change you search into:
index = ad_6mths EventCode="35" OR EventCode="36" OR EventCode="37" OR EventCode="38" source="WinEventLog:System" NOT SourceName="Microsoft-Windows-Time-Service"
Followed by a few NOT <useraccounts>
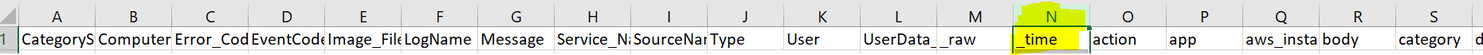
See my result below where N column is _time (Date):
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I also want to point out this only happen when searching in Smart or Verbose Mode. it does not happen in Fast mode.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I did make those changes, but still getting the same thing.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The column order in CSV export depends on the fields of the included events. Therefore your N column might be a completely different thing than my N column (in case of my home windows events export I just did for testing, the N column is "Client_Domain").
But in general - download the CSV and open it in a text editor. Your first row should contain column headers (field names) and the text you pasted seems like field content so either something is wrong with opening the file or it is indeed generated wrongly - open and see.
And it shouldn't have anything to do with Windows TA - CSV export is just export of results. If it's working OK in the WebUI, it should be exported properly.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Can you share your Splunk search?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
index = ad_6mths "EventCode=35" OR "EventCode=36" OR "EventCode=37" OR "EventCode=38" source="WinEventLog:System" NOT "SourceName=Microsoft-Windows-Time-Service"
Followed by a few NOT <useraccounts>